- 15% Off
ESET PROTECT ENTRY On-Prem features
A. ESET ENDPOINT SECURITY
Antivirus and Antispyware
Eliminates all types of threats, including viruses, rootkits, worms and spyware
Optional cloud-powered scanning:
Whitelisting of safe files based on file reputation database in the cloud for better detection and faster scanning. Only information about executable and archive files is sent to the cloud – such data are not personally attributable.
Virtualization Support
ESET Shared Local Cache stores metadata about already scanned files within the virtual environment so identical files are not scanned again, resulting in boosted scan speed.
ESET module updates and virus signatures database are stored outside of the default location, so these don’t have to be downloaded every time a virtual machine is reverted to default snapshot.
Host-Based Intrusion Prevention System (HIPS)
Enables you to define rules for system registry, processes, applications and files. Provides anti-tamper protection and detects threats based on system behavior.
Exploit Blocker
Strengthens security of applications such as web browsers, PDF readers, email clients or MS office components, which are commonly exploited.
Monitors process behaviors and looks for suspicious activities typical of exploits.
Strengthens protection against targeted attacks and previously unknown exploits, i.e. zero-day attacks that could be used by crypto-ransomware to enter the targeted system.
Advanced Memory Scanner
Monitors the behavior of malicious processes and scans them once they decloak in the memory. This allows for effective infection prevention, even from heavily obfuscated malware,
often detecting crypto-ransomware prior to it encrypting valuable files.
Client Antispam
Effectively filters out spam and scans all incoming emails for malware. Native support for Microsoft Outlook (POP3, IMAP, MAPI).
Cross-Platform Protection
ESET security solutions for Windows are capable of detecting Mac OS threats and vice-versa, delivering better protection in multi-platform environments.
Web Control
Limits website access by category, e.g. gaming, social networking, shopping and others. Enables you to create rules for user groups to comply with your company policies.
Soft blocking – notifies the end user that the website is blocked giving him an option to access the website, with activity logged.
Anti-Phishing
Protects end users from attempts by fake websites to acquire sensitive information such as usernames, passwords or banking and credit card details.
Two-Way Firewall
Prevents unauthorized access to your company network. Provides anti-hacker protection and data exposure prevention. Lets you define trusted networks, making all other connections, such as to
public Wi-Fi, in ‘strict’ mode by default. Troubleshooting wizard guides you through a set of questions, identifying problematic rules, or allowing you to create new ones.
Vulnerability Shield
Improves detection of Common Vulnerabilities and Exposures (CVEs) on widely used protocols such as SMB, RPC and RDP.
Protects against vulnerabilities for which a patch has not yet been released or deployed.
Botnet Protection
Protects against infiltration by botnet malware – preventing spam and network attacks launched from the endpoint.
Device Control
Blocks unauthorized devices (CDs/DVDs and USBs) from your system. Enables you to create rules for
user groups to comply with your company policies. Soft blocking – notifies the end user that his device is blocked and gives him the option to access the device, with activity logged.
Idle-State Scanner
Aids system performance by performing a full scan proactively when the computer is not in use. Helps speed up subsequent scans by populating the local cache.
First Scan after Installation
Provides the option to automatically run low priority on-demand scan 20 minutes after installation, assuring protection from the outset.
Update Rollback
Lets you revert to a previous version of protection modules and virus signature database.
Allows you to freeze updates as desired - opt for temporary rollback or delay until manually changed.
Postponed Updates
Provides the option to download from three specialized update servers: pre-release (beta users), regular release (recommended for non-critical systems) and postponed release (recommended for company- critical systems – approximately 12 hours after regular release).
Local Update Server
Saves company bandwidth by downloading updates only once, to a local mirror server.
Mobile workforce updates directly from ESET Update Server when the local mirror is not available. Secured (HTTPS) communication channel is supported.
RIP & Replace
Other security software is detected and uninstalled during installation of ESET Endpoint solutions. Supports both 32 and 64-bit systems.
Customizable GUI Visibility
Visibility of Graphical User Interface (GUI) to end user can be set to: Full, Minimal, Manual or Silent. Presence of ESET solution can be made completely invisible to end user, including no tray icon or notification windows.
By hiding the GUI completely, the “egui.exe” process does not run at all, resulting in even lower system resource consumption by the ESET solution.
ESET License Administrator
Makes it possible to handle all licenses transparently, from one place via web browser. You can merge, delegate and manage all licenses centrally in real-time, even if you are not using ESET Remote Administrator.
Touchscreen Support
Supports touch screens and high-resolution displays.
More padding for and complete rearrangement of GUI elements. Basic frequently used actions accessible from tray menu.
Low System Demands
Delivers proven protection while leaving more system resources for programs that end users regularly run. Can be deployed on older machines without the need for an upgrade, thereby extending hardware lifetime. Conserves battery life for laptops that are away from the office, using battery mode.
Right-to-Left Language Support
Native right-to-left language support (e.g. for Arabic) for optimum usability.
Remote Management
ESET Endpoint solutions are fully manageable via ESET Remote Administrator.
Deploy, run tasks, set up policies, collect logs, and get notifications and an overall security overview of your network – all via a single web-based management console.
- 16% Off
ESET PROTECT ENTRY On-Prem features
A. ESET ENDPOINT SECURITY
Antivirus and Antispyware
Eliminates all types of threats, including viruses, rootkits, worms and spyware
Optional cloud-powered scanning:
Whitelisting of safe files based on file reputation database in the cloud for better detection and faster scanning. Only information about executable and archive files is sent to the cloud – such data are not personally attributable.
Virtualization Support
ESET Shared Local Cache stores metadata about already scanned files within the virtual environment so identical files are not scanned again, resulting in boosted scan speed.
ESET module updates and virus signatures database are stored outside of the default location, so these don’t have to be downloaded every time a virtual machine is reverted to default snapshot.
Host-Based Intrusion Prevention System (HIPS)
Enables you to define rules for system registry, processes, applications and files. Provides anti-tamper protection and detects threats based on system behavior.
Exploit Blocker
Strengthens security of applications such as web browsers, PDF readers, email clients or MS office components, which are commonly exploited.
Monitors process behaviors and looks for suspicious activities typical of exploits.
Strengthens protection against targeted attacks and previously unknown exploits, i.e. zero-day attacks that could be used by crypto-ransomware to enter the targeted system.
Advanced Memory Scanner
Monitors the behavior of malicious processes and scans them once they decloak in the memory. This allows for effective infection prevention, even from heavily obfuscated malware,
often detecting crypto-ransomware prior to it encrypting valuable files.
Client Antispam
Effectively filters out spam and scans all incoming emails for malware. Native support for Microsoft Outlook (POP3, IMAP, MAPI).
Cross-Platform Protection
ESET security solutions for Windows are capable of detecting Mac OS threats and vice-versa, delivering better protection in multi-platform environments.
Web Control
Limits website access by category, e.g. gaming, social networking, shopping and others. Enables you to create rules for user groups to comply with your company policies.
Soft blocking – notifies the end user that the website is blocked giving him an option to access the website, with activity logged.
Anti-Phishing
Protects end users from attempts by fake websites to acquire sensitive information such as usernames, passwords or banking and credit card details.
Two-Way Firewall
Prevents unauthorized access to your company network. Provides anti-hacker protection and data exposure prevention. Lets you define trusted networks, making all other connections, such as to
public Wi-Fi, in ‘strict’ mode by default. Troubleshooting wizard guides you through a set of questions, identifying problematic rules, or allowing you to create new ones.
Vulnerability Shield
Improves detection of Common Vulnerabilities and Exposures (CVEs) on widely used protocols such as SMB, RPC and RDP.
Protects against vulnerabilities for which a patch has not yet been released or deployed.
Botnet Protection
Protects against infiltration by botnet malware – preventing spam and network attacks launched from the endpoint.
Device Control
Blocks unauthorized devices (CDs/DVDs and USBs) from your system. Enables you to create rules for
user groups to comply with your company policies. Soft blocking – notifies the end user that his device is blocked and gives him the option to access the device, with activity logged.
Idle-State Scanner
Aids system performance by performing a full scan proactively when the computer is not in use. Helps speed up subsequent scans by populating the local cache.
First Scan after Installation
Provides the option to automatically run low priority on-demand scan 20 minutes after installation, assuring protection from the outset.
Update Rollback
Lets you revert to a previous version of protection modules and virus signature database.
Allows you to freeze updates as desired - opt for temporary rollback or delay until manually changed.
Postponed Updates
Provides the option to download from three specialized update servers: pre-release (beta users), regular release (recommended for non-critical systems) and postponed release (recommended for company- critical systems – approximately 12 hours after regular release).
Local Update Server
Saves company bandwidth by downloading updates only once, to a local mirror server.
Mobile workforce updates directly from ESET Update Server when the local mirror is not available. Secured (HTTPS) communication channel is supported.
RIP & Replace
Other security software is detected and uninstalled during installation of ESET Endpoint solutions. Supports both 32 and 64-bit systems.
Customizable GUI Visibility
Visibility of Graphical User Interface (GUI) to end user can be set to: Full, Minimal, Manual or Silent. Presence of ESET solution can be made completely invisible to end user, including no tray icon or notification windows.
By hiding the GUI completely, the “egui.exe” process does not run at all, resulting in even lower system resource consumption by the ESET solution.
ESET License Administrator
Makes it possible to handle all licenses transparently, from one place via web browser. You can merge, delegate and manage all licenses centrally in real-time, even if you are not using ESET Remote Administrator.
Touchscreen Support
Supports touch screens and high-resolution displays.
More padding for and complete rearrangement of GUI elements. Basic frequently used actions accessible from tray menu.
Low System Demands
Delivers proven protection while leaving more system resources for programs that end users regularly run. Can be deployed on older machines without the need for an upgrade, thereby extending hardware lifetime. Conserves battery life for laptops that are away from the office, using battery mode.
Right-to-Left Language Support
Native right-to-left language support (e.g. for Arabic) for optimum usability.
Remote Management
ESET Endpoint solutions are fully manageable via ESET Remote Administrator.
Deploy, run tasks, set up policies, collect logs, and get notifications and an overall security overview of your network – all via a single web-based management console.
- 17% Off
The ESET difference
No server required
ESET Endpoint Encryption requires no server for deployment and can seamlessly support remote users.
No special hardware required
TPM chips are optional but not required for using full disk encryption.
Fully validated
ESET Endpoint Encryption is FIPS 140-2 validated with 256 bit AES encryption.
Multi-platform
Encryption supported across Windows 10, 8, 8.1, 7, Vista, XP, and Server 2003 – Server 2016 and iOS.
- 21% Off
The ESET difference
No server required
ESET Endpoint Encryption requires no server for deployment and can seamlessly support remote users.
No special hardware required
TPM chips are optional but not required for using full disk encryption.
Fully validated
ESET Endpoint Encryption is FIPS 140-2 validated with 256 bit AES encryption.
Multi-platform
Encryption supported across Windows 10, 8, 8.1, 7, Vista, XP, and Server 2003 – Server 2016 and iOS.

- 20% Off
Endpoint Encryption by ESET is a simple-to-use encryption application for companies large and small. Take advantage of the optimized setup that speeds up the time to adoption for admins. The client side requires minimal user interaction, increasing user compliance and the security of your company data.
Data encryption for files on hard drives, portable devices and sent via email
- Simple and powerful encryption for organizations of all sizes
- Safely encrypt hard drives, removable media, files and email
- FIPS 140-2 Validated 256 bit AES encryption for assured security
- Hybrid-cloud based management server for full remote control of endpoint encryption keys and security policy
- Support for Microsoft Windows 10, 8, 8.1 including UEFI and GPT
How Endpoint Encryption can help your business
- Meet data security obligations by easily enforcing encryption policies while keeping productivity high.
- Companies large and small benefit with low help-desk overhead and short deployment cycles.
- No other product can match Endpoint Encryption+ for flexibility and ease of use.
- The client side requires minimal user interaction, improving compliance and the security of your company data from a single MSI package.
- The server side makes it easy to manage users and workstations and extend the protection of your company beyond the perimeter of your network.
The GDPR: Encryption as a solution
Do you do business in the European Union? The EU's General Data Protection Regulation (GDPR) comes into force in May 2018, and introduces significant new penalties for organizations that fail to protect their users' data adequately. One proven solution for data protection is encryption.
- Endpoint Encryption by ESET makes encryption of data on hard drives, portable devices and sent via email easy, helping you comply with the GDPR.
- ESET offers online resources, webinars and a compliance checker that you can access for free.
- ESET's GDPR white paper explains key points of the new law, and how to begin preparing now.
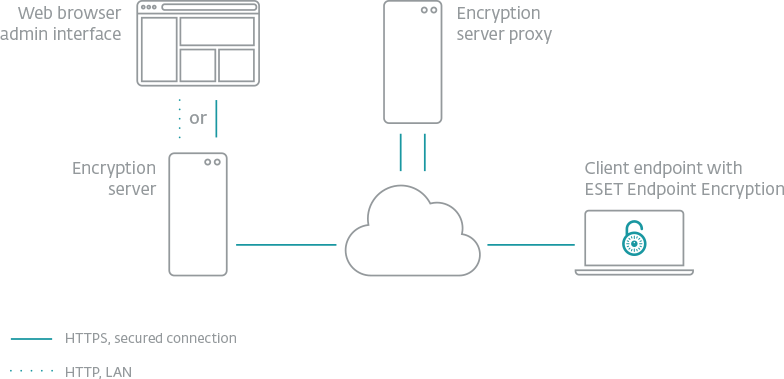
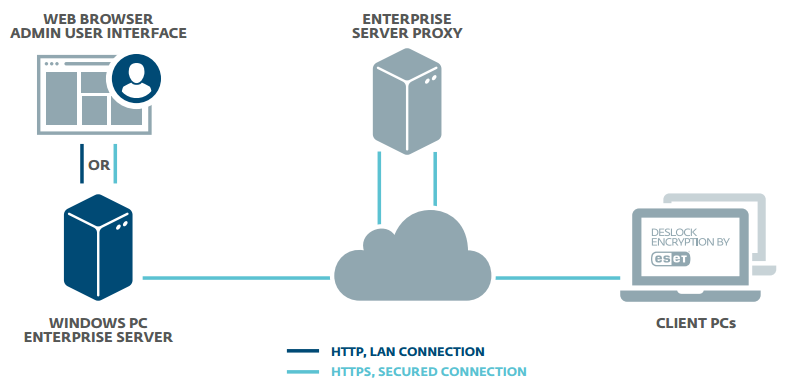
Client Side
Data is a critical part of every organization, but this most valuable asset often poses a huge risk when it travels or is transmitted beyond the corporate network. Full disk and removable media encryption protect laptop computers against the unexpected. File, folder and email encryption allow fully secure collaboration across complex workgroups and team boundaries, with security policy enforced at all endpoints by the Endpoint Encryption+ Enterprise Server. Meet your data security compliance obligations with a single MSI package.
- Full disk and removable media encryption protects data stored or sent using laptop computers
- File, folder and email encryption enables fully secure collaboration across complex workgroups and team boundaries
- Security policy enforcement deployable at all endpoints by the Endpoint Encryption+ Enterprise Server
- A single MSI package allows to meet data security compliance obligations.
Server Side
The Endpoint Encryption+ Enterprise server can manage users and workstations together or independently. Activation, and changes to security policy, software feature-set, encryption keys and endpoint status are all handled, securely through the cloud keeping your most high-risk endpoints under close control at all times Home and mobile working make extending encryption security policy beyond the perimeter of your network a necessity. Only Endpoint Encryption+ offers full control wherever your users are.
- Secure https internet connectivity allows centralized management of users, endpoints and mobile devices beyond your corporate network
- Uniquely patented Security key management, allows full control of encryption keys and encryption security policy remotely and silently
- Patented hybrid cloud architecture means that all client and server connections are SSL encrypted, and all commands and data are AES or RSA encrypted
- Quick install and low system requirements bring enterprise grade security to even the smallest organizations
- 13% Off
Endpoint Encryption by ESET is a simple-to-use encryption application for companies large and small. Take advantage of the optimized setup that speeds up the time to adoption for admins. The client side requires minimal user interaction, increasing user compliance and the security of your company data.
Data encryption for files on hard drives, portable devices and sent via email
- Simple and powerful encryption for organizations of all sizes
- Safely encrypt hard drives, removable media, files and email
- FIPS 140-2 Validated 256 bit AES encryption for assured security
- Hybrid-cloud based management server for full remote control of endpoint encryption keys and security policy
- Support for Microsoft Windows 10, 8, 8.1 including UEFI and GPT
How Endpoint Encryption can help your business
- Meet data security obligations by easily enforcing encryption policies while keeping productivity high.
- Companies large and small benefit with low help-desk overhead and short deployment cycles.
- No other product can match Endpoint Encryption+ for flexibility and ease of use.
- The client side requires minimal user interaction, improving compliance and the security of your company data from a single MSI package.
- The server side makes it easy to manage users and workstations and extend the protection of your company beyond the perimeter of your network.
The GDPR: Encryption as a solution
Do you do business in the European Union? The EU's General Data Protection Regulation (GDPR) comes into force in May 2018, and introduces significant new penalties for organizations that fail to protect their users' data adequately. One proven solution for data protection is encryption.
- Endpoint Encryption by ESET makes encryption of data on hard drives, portable devices and sent via email easy, helping you comply with the GDPR.
- ESET offers online resources, webinars and a compliance checker that you can access for free.
- ESET's GDPR white paper explains key points of the new law, and how to begin preparing now.
Client Side
Data is a critical part of every organization, but this most valuable asset often poses a huge risk when it travels or is transmitted beyond the corporate network. Full disk and removable media encryption protect laptop computers against the unexpected. File, folder and email encryption allow fully secure collaboration across complex workgroups and team boundaries, with security policy enforced at all endpoints by the Endpoint Encryption+ Enterprise Server. Meet your data security compliance obligations with a single MSI package.
- Full disk and removable media encryption protects data stored or sent using laptop computers
- File, folder and email encryption enables fully secure collaboration across complex workgroups and team boundaries
- Security policy enforcement deployable at all endpoints by the Endpoint Encryption+ Enterprise Server
- A single MSI package allows to meet data security compliance obligations.
Server Side
The Endpoint Encryption+ Enterprise server can manage users and workstations together or independently. Activation, and changes to security policy, software feature-set, encryption keys and endpoint status are all handled, securely through the cloud keeping your most high-risk endpoints under close control at all times Home and mobile working make extending encryption security policy beyond the perimeter of your network a necessity. Only Endpoint Encryption+ offers full control wherever your users are.
- Secure https internet connectivity allows centralized management of users, endpoints and mobile devices beyond your corporate network
- Uniquely patented Security key management, allows full control of encryption keys and encryption security policy remotely and silently
- Patented hybrid cloud architecture means that all client and server connections are SSL encrypted, and all commands and data are AES or RSA encrypted
- Quick install and low system requirements bring enterprise grade security to even the smallest organisations

- 60% Off
Endpoint Encryption Essentials Edition 1 User, 1 Year Subscription - features File and Folder Encryption, Mail Encryption, Text and Clipboard Encryption, Virtual Disks and Compressed Archives, Encryption Key Management
Endpoint Encryption Essentials Edition 1 User, 1 Year Subscription - features File and Folder Encryption, Mail Encryption, Text and Clipboard Encryption, Virtual Disks and Compressed Archives, Encryption Key Management
Data is an integral part of modern business. When data is moved from place to place, whether it's via the internet or physical storage, it is vulnerable. Proactively protect your data with ESET Endpoint Encryption.
ESET Endpoint Encryption comes in three forms: Essential, Standard and Pro. Whether your business is large or small one of our packages will suit your needs. With optimised setup, which speeds up adoption times for admins, and a client that requires minimal user interaction, Endpoint Encryption increases user compliance and the security of your company data.
With Endpoint Encryption, you can meet your data security compliance obligations with a single MSI package. Full disk and removable media encryption keeps your data safe on the road. File, folder and email encryption keeps any collaboration across your established workgroups and teams secure; with your security policy enforced at all endpoints by the Endpoint Encryption Enterprise Server.
Manage users and workstations together or independently with the Endpoint Encryption Enterprise server. Keep your most high-risk endpoints under close control at all times: activation and changes to security policy, software feature-set, encryption keys and endpoint status are all handled securely through the cloud to simplify control. Only Endpoint Encryption offers full control wherever your users are allowing employees to work from home or on the move whilst enjoying the full protection of Endpoint Encryption.
Product Features Include:
• File and Folder Encryption ensuring that your teams and workgroups can collaborate securely.
• Mail Encryption ensures that only its intended recipient reads your email.
• Text and Clipboard Encryption ensures that sensitive information can't be read from the clipboard.
• Virtual Disks and Compressed Archives ensure that information sent on CD/DVD's or via an FTP server is secure.
• Encryption Key Management allows you to add or remove encryption keys with ease, without affecting the user.
• Centralised Management helps you manage every endpoint user and workstation from a single centralised hub.
• Enterprise Server Proxy can act as an intermediary ensuring that all connections from the client and server are outgoing.
Data is an integral part of modern business. When data is moved from place to place, whether it's via the internet or physical storage, it is vulnerable. Proactively protect your data with ESET Endpoint Encryption.
ESET Endpoint Encryption comes in three forms: Essential, Standard and Pro. Whether your business is large or small one of our packages will suit your needs. With optimised setup, which speeds up adoption times for admins, and a client that requires minimal user interaction, Endpoint Encryption increases user compliance and the security of your company data.
With Endpoint Encryption, you can meet your data security compliance obligations with a single MSI package. Full disk and removable media encryption keeps your data safe on the road. File, folder and email encryption keeps any collaboration across your established workgroups and teams secure; with your security policy enforced at all endpoints by the Endpoint Encryption Enterprise Server.
Manage users and workstations together or independently with the Endpoint Encryption Enterprise server. Keep your most high-risk endpoints under close control at all times: activation and changes to security policy, software feature-set, encryption keys and endpoint status are all handled securely through the cloud to simplify control. Only Endpoint Encryption offers full control wherever your users are allowing employees to work from home or on the move whilst enjoying the full protection of Endpoint Encryption.
Product Features Include:
• File and Folder Encryption ensuring that your teams and workgroups can collaborate securely.
• Mail Encryption ensures that only its intended recipient reads your email.
• Text and Clipboard Encryption ensures that sensitive information can't be read from the clipboard.
• Virtual Disks and Compressed Archives ensure that information sent on CD/DVD's or via an FTP server is secure.
• Encryption Key Management allows you to add or remove encryption keys with ease, without affecting the user.
• Centralised Management helps you manage every endpoint user and workstation from a single centralised hub.
• Enterprise Server Proxy can act as an intermediary ensuring that all connections from the client and server are outgoing.
- 29% Off
Endpoint Encryption Essentials Edition 1 User, 1 Year Subscription - features File and Folder Encryption, Mail Encryption, Text and Clipboard Encryption, Virtual Disks and Compressed Archives, Encryption Key Management
Data is an integral part of modern business. When data is moved from place to place, whether it's via the internet or physical storage, it is vulnerable. Proactively protect your data with ESET Endpoint Encryption.
ESET Endpoint Encryption comes in three forms: Essential, Standard and Pro. Whether your business is large or small one of our packages will suit your needs. With optimised setup, which speeds up adoption times for admins, and a client that requires minimal user interaction, Endpoint Encryption increases user compliance and the security of your company data.
With Endpoint Encryption, you can meet your data security compliance obligations with a single MSI package. Full disk and removable media encryption keeps your data safe on the road. File, folder and email encryption keeps any collaboration across your established workgroups and teams secure; with your security policy enforced at all endpoints by the Endpoint Encryption Enterprise Server.
Manage users and workstations together or independently with the Endpoint Encryption Enterprise server. Keep your most high-risk endpoints under close control at all times: activation and changes to security policy, software feature-set, encryption keys and endpoint status are all handled securely through the cloud to simplify control. Only Endpoint Encryption offers full control wherever your users are allowing employees to work from home or on the move whilst enjoying the full protection of Endpoint Encryption.
Product Features Include:
• File and Folder Encryption ensuring that your teams and workgroups can collaborate securely.
• Mail Encryption ensures that only its intended recipient reads your email.
• Text and Clipboard Encryption ensures that sensitive information can't be read from the clipboard.
• Virtual Disks and Compressed Archives ensure that information sent on CD/DVD's or via an FTP server is secure.
• Encryption Key Management allows you to add or remove encryption keys with ease, without affecting the user.
• Centralised Management helps you manage every endpoint user and workstation from a single centralised hub.
• Enterprise Server Proxy can act as an intermediary ensuring that all connections from the client and server are outgoing.
- 30% Off
ESET Secure Authentication provides powerful software-based two-factor authentication (2FA), safeguarding your company’s mobile workforce against data breaches due to compromised passwords and aiding in regulatory compliance with HIPAA, PCI DSS and NIST. ESET Secure Authentication validates each VPN and Outlook Web Access (OWA) login with a unique one-time-password (OTP) adding an important layer of security to your company’s sensitive data. Simple to manage, ESET Secure Authentication is more flexible, cost effective, and easy to use than hardware OTP tokens or appliances.
ESET Secure Authentication helps businesses access their data securely. Our solution utilizes the existing Active Directory domain, allowing you to set up ESET’s two-factor authentication in just 10 minutes – and thus easily reduce the risk of data breaches, caused by stolen, weak or compromised passwords.
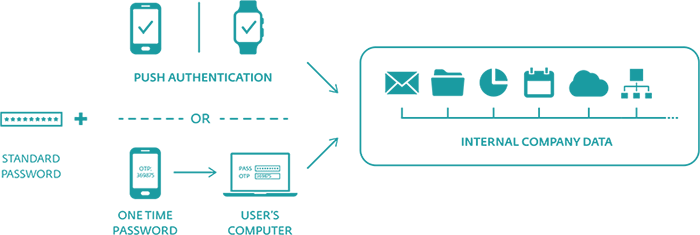
The solution consists of the server side and the client side – the latter comes in the form of a mobile app. The authentication options include Push Authentication, as well as generation and delivery one-time passwords (OTPs) via the mobile app, but also via SMS messages or your organization’s existing hardware tokens.
Single-tap authentication for extra data protection
- Two-factor authentication. Prevents security breaches by validating users' identities
- Easy management, fast roll-out. Integrates with Active Directory and ready to use within 10 minutes
- Designed for a mobile world. No extra hardware required - keeps costs low and users happy
- Compliance with confidence. Helps organizations comply with regulations such as GDPR or PCI-DSS/HIPAA
- Created with business productivity in mind. Our flexible integration options offer 2FA whenever identities or transactions need protecting
ESET Secure Authentication helps you secure your data in a hassle-free way. By complementing your normal authentication with a second factor, it effectively reduces the risk of data breaches caused by weak or leaked passwords.
Use ESET Secure Authentication to protect:
- Access to your company’s VPN
- Remote Desktop Protocol
- Additional authentication for desktop login (signing into an operating system)
- Web/cloud services via Microsoft ADFS 3.0, such as Office 365
- Microsoft Web Apps, such as OWA
- Exchange Control Panel & Exchange Administrator Center
- VMware Horizon View
- RADIUS-based services
Easy integration with your RADIUS-based services or via an API to your existing Active Directory-based authentication. Non Active Directory customers with custom systems can use the easy-to-deploy SDK.
- 19% Off
ESET Secure Authentication provides powerful software-based two-factor authentication (2FA), safeguarding your company’s mobile workforce against data breaches due to compromised passwords and aiding in regulatory compliance with HIPAA, PCI DSS and NIST. ESET Secure Authentication validates each VPN and Outlook Web Access (OWA) login with a unique one-time-password (OTP) adding an important layer of security to your company’s sensitive data. Simple to manage, ESET Secure Authentication is more flexible, cost effective, and easy to use than hardware OTP tokens or appliances.
ESET Secure Authentication helps businesses access their data securely. Our solution utilizes the existing Active Directory domain, allowing you to set up ESET’s two-factor authentication in just 10 minutes – and thus easily reduce the risk of data breaches, caused by stolen, weak or compromised passwords.
The solution consists of the server side and the client side – the latter comes in the form of a mobile app. The authentication options include Push Authentication, as well as generation and delivery one-time passwords (OTPs) via the mobile app, but also via SMS messages or your organization’s existing hardware tokens.
Single-tap authentication for extra data protection
- Two-factor authentication. Prevents security breaches by validating users' identities
- Easy management, fast roll-out. Integrates with Active Directory and ready to use within 10 minutes
- Designed for a mobile world. No extra hardware required - keeps costs low and users happy
- Compliance with confidence. Helps organizations comply with regulations such as GDPR or PCI-DSS/HIPAA
- Created with business productivity in mind. Our flexible integration options offer 2FA whenever identities or transactions need protecting

ESET Secure Authentication helps you secure your data in a hassle-free way. By complementing your normal authentication with a second factor, it effectively reduces the risk of data breaches caused by weak or leaked passwords.
Use ESET Secure Authentication to protect:
- Access to your company’s VPN
- Remote Desktop Protocol
- Additional authentication for desktop login (signing into an operating system)
- Web/cloud services via Microsoft ADFS 3.0, such as Office 365
- Microsoft Web Apps, such as OWA
- Exchange Control Panel & Exchange Administrator Center
- VMware Horizon View
- RADIUS-based services
Easy integration with your RADIUS-based services or via an API to your existing Active Directory-based authentication. Non Active Directory customers with custom systems can use the easy-to-deploy SDK.
- 15% Off
1-Year Subscription License. Includes all Product updates, Full version upgrades, Virus definition updates and technical support.
Symantec Endpoint Protection 14 fuses Artificial intelligence with critical endpoint technologies to deliver the most complete endpoint security on the planet.
Stronger, faster, lighter
- Symantec Endpoint Protection 14 reduces bandwidth usage and definition file sizes by 70 percent over previous versions.
- Our proprietary real-time cloud lookup enables faster scanning times.
- Supports machine learning, exploit prevention, Endpoint Detection and Response (EDR), and antimalware, from one single agent.
- Reduce total cost of ownership and IT resources via automated updates.
- READ THE REPORT
Respond and protect at scale
- Integrates seamlessly with Symantec Blue Coat ProxySG web gateway and other security controls via programmable APIs to respond smartly at the endpoint.
- See and manage all your endpoints from a single high-performance agent and management console for Windows, Mac, Linux, virtual machines, and embedded systems.
- Ensure the most current protection with self-updating endpoint agents and extended LiveUpdate Administrator capabilities to support security patching.
175 million endpoints at your service
- Symantec's global intelligence network of 175 million endpoints and our advanced machine learning technologies allow you to detect threats more accurately.
- Advanced machine learning done right: Stop unknown threats with advanced machine learning AI to deliver maximum protection at the endpoint with minimal false positives.
- Wrap your endpoints in multi-layered protection—artificial intelligence in the cloud, combined with critical endpoint technologies creates the most threat-resistant endpoint security in the world.
- Block zero-day attacks that prey on memory-based vulnerabilities in many popular applications with memory exploit mitigation.
For more information, download the Symantec Endpoint Protection 14 datasheet here.
- 26% Off
3-Year Subscription License. Includes all Product updates, Full version upgrades, Virus definition updates and technical support.
Symantec Endpoint Protection 14 fuses Artificial intelligence with critical endpoint technologies to deliver the most complete endpoint security on the planet.
Stronger, faster, lighter
- Symantec Endpoint Protection 14 reduces bandwidth usage and definition file sizes by 70 percent over previous versions.
- Our proprietary real-time cloud lookup enables faster scanning times.
- Supports machine learning, exploit prevention, Endpoint Detection and Response (EDR), and antimalware, from one single agent.
- Reduce total cost of ownership and IT resources via automated updates.
- READ THE REPORT
Respond and protect at scale
- Integrates seamlessly with Symantec Blue Coat ProxySG web gateway and other security controls via programmable APIs to respond smartly at the endpoint.
- See and manage all your endpoints from a single high-performance agent and management console for Windows, Mac, Linux, virtual machines, and embedded systems.
- Ensure the most current protection with self-updating endpoint agents and extended LiveUpdate Administrator capabilities to support security patching.
175 million endpoints at your service
- Symantec's global intelligence network of 175 million endpoints and our advanced machine learning technologies allow you to detect threats more accurately.
- Advanced machine learning done right: Stop unknown threats with advanced machine learning AI to deliver maximum protection at the endpoint with minimal false positives.
- Wrap your endpoints in multi-layered protection—artificial intelligence in the cloud, combined with critical endpoint technologies creates the most threat-resistant endpoint security in the world.
- Block zero-day attacks that prey on memory-based vulnerabilities in many popular applications with memory exploit mitigation.
For more information, download the Symantec Endpoint Protection 14 datasheet here.
- 17% Off
1-Year Subscription License. Includes all Product updates, Full version upgrades, Virus definition updates and technical support.
Symantec Endpoint Security Enterprise offers Industry-leading protection for all devices with cloud, on-premises, or hybrid management.
Symantec Endpoint Security Enterprise delivers the most complete, integrated endpoint security platform on the planet. As an on-premises, hybrid, or cloud-based solution, the single-agent Symantec platform protects all your traditional and mobile endpoint devices, and uses artificial intelligence (AI) to optimize security decisions. A unified cloud-based management system simplifies protecting, detecting and responding to all the advanced threats targeting your endpoints.
- Keep your business running. Compromised endpoints are highly disruptive to business. Innovative attack prevention and attack surface reduction delivers the strongest security across the entire attack life cycle (e.g., stealthy malware, credential theft, fileless, and “living off the land” attacks).
- Prevent the worst-case scenario. Full blown breaches are CISOs' worst nightmare. Deliver detection and remediation of persistent threats with sophisticated attack analytics and prevention of AD credential theft.
- Manage smarter. Work less. Intelligent automation and AI-guided policy management enhance administrator productivity; Symantec experts fortify SOC teams to meet customer needs without hiring additional headcount.
- Manage everything in one place. Integrated Cyber Defense Manager (ICDm) is a single cloud management console that strengthens overall endpoint security posture.
- Endpoint security delivered your way. With a single agent, protection across traditional and mobile devices, and on-prem, cloud or hybrid management.
Click here to download a datasheet on Symantec Endpoint Security.
- 20% Off
3-Year Subscription License. Includes all Product updates, Full version upgrades, Virus definition updates and technical support.
Symantec Endpoint Security Enterprise offers Industry-leading protection for all devices with cloud, on-premises, or hybrid management.
Symantec Endpoint Security Enterprise delivers the most complete, integrated endpoint security platform on the planet. As an on-premises, hybrid, or cloud-based solution, the single-agent Symantec platform protects all your traditional and mobile endpoint devices, and uses artificial intelligence (AI) to optimize security decisions. A unified cloud-based management system simplifies protecting, detecting and responding to all the advanced threats targeting your endpoints.
- Keep your business running. Compromised endpoints are highly disruptive to business. Innovative attack prevention and attack surface reduction delivers the strongest security across the entire attack life cycle (e.g., stealthy malware, credential theft, fileless, and “living off the land” attacks).
- Prevent the worst-case scenario. Full blown breaches are CISOs' worst nightmare. Deliver detection and remediation of persistent threats with sophisticated attack analytics and prevention of AD credential theft.
- Manage smarter. Work less. Intelligent automation and AI-guided policy management enhance administrator productivity; Symantec experts fortify SOC teams to meet customer needs without hiring additional headcount.
- Manage everything in one place. Integrated Cyber Defense Manager (ICDm) is a single cloud management console that strengthens overall endpoint security posture.
- Endpoint security delivered your way. With a single agent, protection across traditional and mobile devices, and on-prem, cloud or hybrid management.
Click here to download a datasheet on Symantec Endpoint Security.
- 8% Off
1-Year Subscription License. Includes all Product updates, Full version upgrades, Virus definition updates and technical support.
Prevent attacks early in the attack chain before a full breach occurs. Only Symantec delivers attack and breach prevention, response and remediation across the attack chain.
Symantec Endpoint Security Complete provides your organization with ultimate security at the endpoint. It stops endpoint compromise with superior next gen protection technologies that span the attack chain. Innovative prevention and proactive attack surface reduction technologies provide the strongest defense against the hardest to detect threats that rely on stealthy malware, credential theft, fileless, and “living off the land” attack methods. Symantec also prevents full-blown breaches before exfiltration can occur. Sophisticated attack analytics, automated investigation playbooks, and industry first lateral movement and credential theft prevention provide precise attack detections and proactive threat hunting to contain the attacker and resolve persistent threats in real time.
Protections for All Phases of the Attack Lifecycle
Pre-Attack Surface Reduction
Proactive endpoint defense with pre-attack surface reduction capabilities based on advanced policy controls and technologies continuously scan for vulnerabilities and misconfigurations across applications, Active Directory, and devices. With attack surface reduction defenses in-place, many attacker tactics and techniques cannot be leveraged on your endpoint estate.
- Vulnerability Remediation enhances your security posture by providing visibility and intelligence into vulnerabilities and their associated risk.
- Breach Assessment continuously probes Active Directory for domain misconfigurations, vulnerabilities, and persistence using attack simulations to identify risks.
- Device Control specifies block or allow policies on different types of devices that attach to client computers, such as USB, infrared, and FireWire devices.
- App Isolation & App Control allows only known good applications to run, shields known-good applications to prevent attackers from exploiting application vulnerabilities, and isolates unknown apps.
Attack Prevention
Multilayer attack prevention immediately and effectively protects against file-based and fileless attack vectors and methods. Machine learning and artificial intelligence use advanced device and cloud-based detection schemes to identify evolving threats across device types, operating systems, and applications. Attacks are blocked in real-time to maintain endpoint integrity and avoid negative impacts.
- Malware Prevention combines signature-based methods (file and website reputation analysis and antivirus scanning) and pre-execution detection and blocking of new and evolving threats (advanced machine learning, sandboxing to detect malware hidden in custom packers, and suspicious file behavioral monitoring and blocking).
- Exploit Prevention blocks memory-based zero-day exploits of vulnerabilities in popular software.
- Intensive Protection enables fine-grained tuning of the level of detection and blocking separately to optimize protection and gain enhanced visibility into suspicious files.
- Network Connection Security identifies rogue Wi-Fi networks and utilizes hotspot reputation technology and delivers a policy-driven VPN to protect network connections and support compliance.
Breach Prevention
Proactive endpoint defense with pre-attack surface reduction capabilities based on advanced policy controls and technologies continuously scan for vulnerabilities and misconfigurations across applications, Active Directory, and devices. With attack surface reduction defenses in-place, many attacker tactics and techniques cannot be leveraged on your endpoint estate.
- Vulnerability Remediation enhances your security posture by providing visibility and intelligence into vulnerabilities and their associated risk.
- Breach Assessment continuously probes Active Directory for domain misconfigurations, vulnerabilities, and persistence using attack simulations to identify risks.
- Device Control specifies block or allow policies on different types of devices that attach to client computers, such as USB, infrared, and FireWire devices.
- App Isolation & App Control allows only known good applications to run, shields known-good applications to prevent attackers from exploiting application vulnerabilities, and isolates unknown apps.
Response and Remediation
Proactive endpoint defense with pre-attack surface reduction capabilities based on advanced policy controls and technologies continuously scan for vulnerabilities and misconfigurations across applications, Active Directory, and devices. With attack surface reduction defenses in-place, many attacker tactics and techniques cannot be leveraged on your endpoint estate.
- Vulnerability Remediation enhances your security posture by providing visibility and intelligence into vulnerabilities and their associated risk.
- Breach Assessment continuously probes Active Directory for domain misconfigurations, vulnerabilities, and persistence using attack simulations to identify risks.
- Device Control specifies block or allow policies on different types of devices that attach to client computers, such as USB, infrared, and FireWire devices.
- App Isolation & App Control allows only known good applications to run, shields known-good applications to prevent attackers from exploiting application vulnerabilities, and isolates unknown apps.
Click here to download a datasheet on Symantec Endpoint Security.