Technical Specifications
Compare the feature set of Sophos’s various endpoint products to protect your clients. Not sure which protection best suits your business? We advise you free of charge and completely without obligation.
ESET Endpoint Encryption requires no server for deployment and can seamlessly support remote users.
TPM chips are optional but not required for using full disk encryption.
ESET Endpoint Encryption is FIPS 140-2 validated with 256 bit AES encryption.
Encryption supported across Windows 10, 8, 8.1, 7, Vista, XP, and Server 2003 – Server 2016 and iOS.
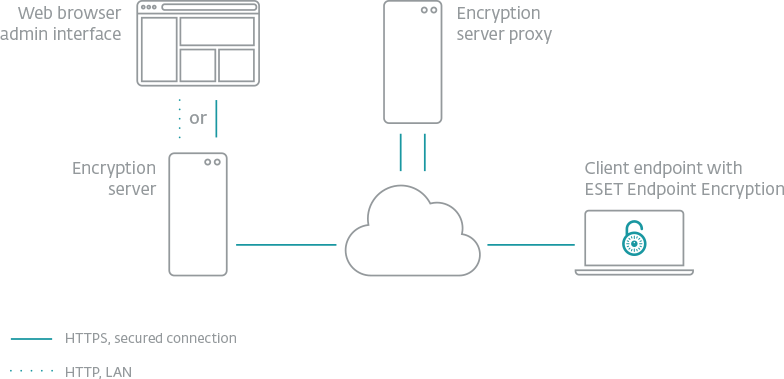
Endpoint Encryption by ESET is a simple-to-use encryption application for companies large and small. Take advantage of the optimized setup that speeds up the time to adoption for admins. The client side requires minimal user interaction, increasing user compliance and the security of your company data.
Do you do business in the European Union? The EU's General Data Protection Regulation (GDPR) comes into force in May 2018, and introduces significant new penalties for organizations that fail to protect their users' data adequately. One proven solution for data protection is encryption.
Data is a critical part of every organization, but this most valuable asset often poses a huge risk when it travels or is transmitted beyond the corporate network. Full disk and removable media encryption protect laptop computers against the unexpected. File, folder and email encryption allow fully secure collaboration across complex workgroups and team boundaries, with security policy enforced at all endpoints by the Endpoint Encryption+ Enterprise Server. Meet your data security compliance obligations with a single MSI package.
The Endpoint Encryption+ Enterprise server can manage users and workstations together or independently. Activation, and changes to security policy, software feature-set, encryption keys and endpoint status are all handled, securely through the cloud keeping your most high-risk endpoints under close control at all times Home and mobile working make extending encryption security policy beyond the perimeter of your network a necessity. Only Endpoint Encryption+ offers full control wherever your users are.
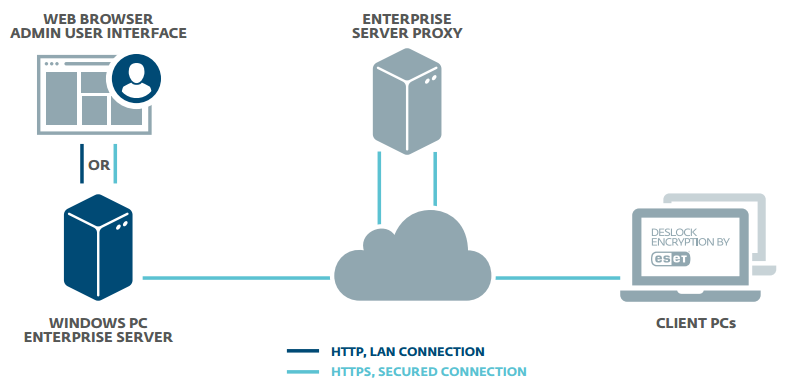
Endpoint Encryption by ESET is a simple-to-use encryption application for companies large and small. Take advantage of the optimized setup that speeds up the time to adoption for admins. The client side requires minimal user interaction, increasing user compliance and the security of your company data.
Do you do business in the European Union? The EU's General Data Protection Regulation (GDPR) comes into force in May 2018, and introduces significant new penalties for organizations that fail to protect their users' data adequately. One proven solution for data protection is encryption.
Data is a critical part of every organization, but this most valuable asset often poses a huge risk when it travels or is transmitted beyond the corporate network. Full disk and removable media encryption protect laptop computers against the unexpected. File, folder and email encryption allow fully secure collaboration across complex workgroups and team boundaries, with security policy enforced at all endpoints by the Endpoint Encryption+ Enterprise Server. Meet your data security compliance obligations with a single MSI package.
The Endpoint Encryption+ Enterprise server can manage users and workstations together or independently. Activation, and changes to security policy, software feature-set, encryption keys and endpoint status are all handled, securely through the cloud keeping your most high-risk endpoints under close control at all times Home and mobile working make extending encryption security policy beyond the perimeter of your network a necessity. Only Endpoint Encryption+ offers full control wherever your users are.

Endpoint Encryption Essentials Edition 1 User, 1 Year Subscription - features File and Folder Encryption, Mail Encryption, Text and Clipboard Encryption, Virtual Disks and Compressed Archives, Encryption Key Management
Data is an integral part of modern business. When data is moved from place to place, whether it's via the internet or physical storage, it is vulnerable. Proactively protect your data with ESET Endpoint Encryption.
ESET Endpoint Encryption comes in three forms: Essential, Standard and Pro. Whether your business is large or small one of our packages will suit your needs. With optimised setup, which speeds up adoption times for admins, and a client that requires minimal user interaction, Endpoint Encryption increases user compliance and the security of your company data.
With Endpoint Encryption, you can meet your data security compliance obligations with a single MSI package. Full disk and removable media encryption keeps your data safe on the road. File, folder and email encryption keeps any collaboration across your established workgroups and teams secure; with your security policy enforced at all endpoints by the Endpoint Encryption Enterprise Server.
Manage users and workstations together or independently with the Endpoint Encryption Enterprise server. Keep your most high-risk endpoints under close control at all times: activation and changes to security policy, software feature-set, encryption keys and endpoint status are all handled securely through the cloud to simplify control. Only Endpoint Encryption offers full control wherever your users are allowing employees to work from home or on the move whilst enjoying the full protection of Endpoint Encryption.
Product Features Include:
• File and Folder Encryption ensuring that your teams and workgroups can collaborate securely.
• Mail Encryption ensures that only its intended recipient reads your email.
• Text and Clipboard Encryption ensures that sensitive information can't be read from the clipboard.
• Virtual Disks and Compressed Archives ensure that information sent on CD/DVD's or via an FTP server is secure.
• Encryption Key Management allows you to add or remove encryption keys with ease, without affecting the user.
• Centralised Management helps you manage every endpoint user and workstation from a single centralised hub.
• Enterprise Server Proxy can act as an intermediary ensuring that all connections from the client and server are outgoing.
Endpoint Encryption Essentials Edition 1 User, 1 Year Subscription - features File and Folder Encryption, Mail Encryption, Text and Clipboard Encryption, Virtual Disks and Compressed Archives, Encryption Key Management
Data is an integral part of modern business. When data is moved from place to place, whether it's via the internet or physical storage, it is vulnerable. Proactively protect your data with ESET Endpoint Encryption.
ESET Endpoint Encryption comes in three forms: Essential, Standard and Pro. Whether your business is large or small one of our packages will suit your needs. With optimised setup, which speeds up adoption times for admins, and a client that requires minimal user interaction, Endpoint Encryption increases user compliance and the security of your company data.
With Endpoint Encryption, you can meet your data security compliance obligations with a single MSI package. Full disk and removable media encryption keeps your data safe on the road. File, folder and email encryption keeps any collaboration across your established workgroups and teams secure; with your security policy enforced at all endpoints by the Endpoint Encryption Enterprise Server.
Manage users and workstations together or independently with the Endpoint Encryption Enterprise server. Keep your most high-risk endpoints under close control at all times: activation and changes to security policy, software feature-set, encryption keys and endpoint status are all handled securely through the cloud to simplify control. Only Endpoint Encryption offers full control wherever your users are allowing employees to work from home or on the move whilst enjoying the full protection of Endpoint Encryption.
Product Features Include:
• File and Folder Encryption ensuring that your teams and workgroups can collaborate securely.
• Mail Encryption ensures that only its intended recipient reads your email.
• Text and Clipboard Encryption ensures that sensitive information can't be read from the clipboard.
• Virtual Disks and Compressed Archives ensure that information sent on CD/DVD's or via an FTP server is secure.
• Encryption Key Management allows you to add or remove encryption keys with ease, without affecting the user.
• Centralised Management helps you manage every endpoint user and workstation from a single centralised hub.
• Enterprise Server Proxy can act as an intermediary ensuring that all connections from the client and server are outgoing.
ESET Secure Authentication provides powerful software-based two-factor authentication (2FA), safeguarding your company’s mobile workforce against data breaches due to compromised passwords and aiding in regulatory compliance with HIPAA, PCI DSS and NIST. ESET Secure Authentication validates each VPN and Outlook Web Access (OWA) login with a unique one-time-password (OTP) adding an important layer of security to your company’s sensitive data. Simple to manage, ESET Secure Authentication is more flexible, cost effective, and easy to use than hardware OTP tokens or appliances.
ESET Secure Authentication helps businesses access their data securely. Our solution utilizes the existing Active Directory domain, allowing you to set up ESET’s two-factor authentication in just 10 minutes – and thus easily reduce the risk of data breaches, caused by stolen, weak or compromised passwords.
The solution consists of the server side and the client side – the latter comes in the form of a mobile app. The authentication options include Push Authentication, as well as generation and delivery one-time passwords (OTPs) via the mobile app, but also via SMS messages or your organization’s existing hardware tokens.
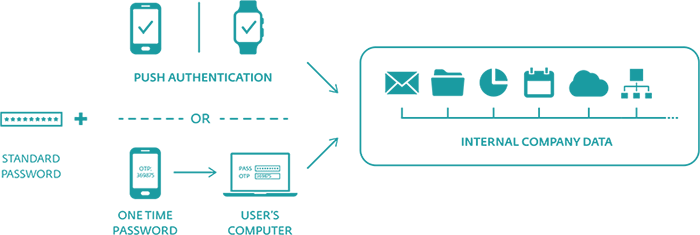
ESET Secure Authentication helps you secure your data in a hassle-free way. By complementing your normal authentication with a second factor, it effectively reduces the risk of data breaches caused by weak or leaked passwords.
Use ESET Secure Authentication to protect:
Easy integration with your RADIUS-based services or via an API to your existing Active Directory-based authentication. Non Active Directory customers with custom systems can use the easy-to-deploy SDK.
ESET Secure Authentication provides powerful software-based two-factor authentication (2FA), safeguarding your company’s mobile workforce against data breaches due to compromised passwords and aiding in regulatory compliance with HIPAA, PCI DSS and NIST. ESET Secure Authentication validates each VPN and Outlook Web Access (OWA) login with a unique one-time-password (OTP) adding an important layer of security to your company’s sensitive data. Simple to manage, ESET Secure Authentication is more flexible, cost effective, and easy to use than hardware OTP tokens or appliances.
ESET Secure Authentication helps businesses access their data securely. Our solution utilizes the existing Active Directory domain, allowing you to set up ESET’s two-factor authentication in just 10 minutes – and thus easily reduce the risk of data breaches, caused by stolen, weak or compromised passwords.
The solution consists of the server side and the client side – the latter comes in the form of a mobile app. The authentication options include Push Authentication, as well as generation and delivery one-time passwords (OTPs) via the mobile app, but also via SMS messages or your organization’s existing hardware tokens.

ESET Secure Authentication helps you secure your data in a hassle-free way. By complementing your normal authentication with a second factor, it effectively reduces the risk of data breaches caused by weak or leaked passwords.
Use ESET Secure Authentication to protect:
Easy integration with your RADIUS-based services or via an API to your existing Active Directory-based authentication. Non Active Directory customers with custom systems can use the easy-to-deploy SDK.
Intercept X Essentials is the new entry-level endpoint protection for small businesses at an affordable price. It offers the same protections as Intercept X Advanced with deep-learning AI, anti-ransomware, and anti-exploit capabilities, but without all the control and management features, which you probably won't miss if your organization is small or perceives low risk.
If you need multiple configurable policies or a higher level of manageability with Peripheral Control, Web Control, Application Control, etc., consider purchasing Intercept X Advanced instead.
Compare the feature set of Sophos’s various endpoint products to protect your clients. Not sure which protection best suits your business? We advise you free of charge and completely without obligation.
Intercept X Essentials is the new entry-level endpoint protection for small businesses at an affordable price. It offers the same protections as Intercept X Advanced with deep-learning AI, anti-ransomware, and anti-exploit capabilities, but without all the control and management features, which you probably won't miss if your organization is small or perceives low risk.
If you need multiple configurable policies or a higher level of manageability with Peripheral Control, Web Control, Application Control, etc., consider purchasing Intercept X Advanced instead.
Compare the feature set of Sophos’s various endpoint products to protect your clients. Not sure which protection best suits your business? We advise you free of charge and completely without obligation.
Sophos Central Intercept X Advanced is a combination of Sophos Central Endpoint Protection and Intercept X products.
With Sophos Central Intercept X Advanced, you get all the features of Sophos Central Endpoint Protection and Intercept X in one product.
On the one hand, you benefit from great functions such as "Peripheral Control" or "Malicious Traffic Detection", and at the same time you get a specialist on your computer with Intercept X, which uses a technology called "CryptoGuard" to detect as soon as malware tries to encrypt files on your computer and stops this process immediately. Files that have already been encrypted are then automatically restored, so there is no data loss.
Would you like to see the Sophos Central user interface live? Just go to central.sophos.com and use the demo account. Username: demo@sophos.com / Password: Demo@sophos.com
Preventing the exploitation of security vulnerabilities.
Sophos Exploit Protection is a unique technology in Intercept X that prevents previously unknown or unpatched vulnerabilities in applications or operating system components from being exploited. With Intercept X, every application is monitored in the background and every action is checked to see if an exploit technique is being attempted.
If such a technique is detected, Exploit Prevention prevents a vulnerability from being exploited and restores the system to a secure state.
Find out the cause of the attack.
Imagine that, despite all the protective measures, malware has made it into your network. How could this happen? Thanks to the root cause analysis in Intercept X, this mystery can be uncovered with an impressive 360-degree analysis. The Root Cause Analysis Tool can tell you in great detail how the malware got into your network, which devices were infected and what steps you should take now.
With root cause analysis, you'll never be in the dark again if your network has been infected by an unknown malware.
Restores the system to its original state after an attack.
With Intercept X, thanks to technologies like CryptoGuard, you are protected against signatureless malware, such as ransomware, but after an attempted attack, your system still needs to be cleaned of all remnants. Since there is no cleaning routine for unknown malware, the entire processes of the executed malware must be forensically examined. This task is performed by Sophos Clean.
Sophos Clean performs a complete cleaning of the system after an attack has been stopped. It not only removes the malware itself, but replaces infected Windows resources with more secure original versions and ultimately restores the system to its original state, as it was before the infection.
Compare the feature set of Sophos’s various endpoint products to protect your clients. Not sure which protection best suits your business? We advise you free of charge and completely without obligation.
Sophos Central Intercept X Advanced is a combination of Sophos Central Endpoint Protection and Intercept X products.
With Sophos Central Intercept X Advanced, you get all the features of Sophos Central Endpoint Protection and Intercept X in one product.
On the one hand, you benefit from great functions such as "Peripheral Control" or "Malicious Traffic Detection", and at the same time you get a specialist on your computer with Intercept X, which uses a technology called "CryptoGuard" to detect as soon as malware tries to encrypt files on your computer and stops this process immediately. Files that have already been encrypted are then automatically restored, so there is no data loss.
Would you like to see the Sophos Central user interface live? Just go to central.sophos.com and use the demo account. Username: demo@sophos.com / Password: Demo@sophos.com
Preventing the exploitation of security vulnerabilities.
Sophos Exploit Protection is a unique technology in Intercept X that prevents previously unknown or unpatched vulnerabilities in applications or operating system components from being exploited. With Intercept X, every application is monitored in the background and every action is checked to see if an exploit technique is being attempted.
If such a technique is detected, Exploit Prevention prevents a vulnerability from being exploited and restores the system to a secure state.
Find out the cause of the attack.
Imagine that, despite all the protective measures, malware has made it into your network. How could this happen? Thanks to the root cause analysis in Intercept X, this mystery can be uncovered with an impressive 360-degree analysis. The Root Cause Analysis Tool can tell you in great detail how the malware got into your network, which devices were infected and what steps you should take now.
With root cause analysis, you'll never be in the dark again if your network has been infected by an unknown malware.
Restores the system to its original state after an attack.
With Intercept X, thanks to technologies like CryptoGuard, you are protected against signatureless malware, such as ransomware, but after an attempted attack, your system still needs to be cleaned of all remnants. Since there is no cleaning routine for unknown malware, the entire processes of the executed malware must be forensically examined. This task is performed by Sophos Clean.
Sophos Clean performs a complete cleaning of the system after an attack has been stopped. It not only removes the malware itself, but replaces infected Windows resources with more secure original versions and ultimately restores the system to its original state, as it was before the infection.
Compare the feature set of Sophos’s various endpoint products to protect your clients. Not sure which protection best suits your business? We advise you free of charge and completely without obligation.
Sophos Intercept X is the industry leading Endpoint Security solution that reduces the attack surface and prevents attacks from running. Combining anti-exploit, anti-ransomware, deep learning AI and control technology it stops attacks before they impact your systems. Intercept X uses a comprehensive, defense in depth approach to endpoint protection, rather than relying on one primary security technique.
Achieve unmatched endpoint threat prevention. Intercept X uses deep learning, an advanced form of machine learning to detect both known and unknown malware without relying on signatures.
Deep learning makes Intercept X smarter, more scalable, and more effective against never-seen-before threats. Intercept X leverages deep learning to outperform endpoint security solutions that use traditional machine learning or signature-based detection alone.
Block ransomware attacks before they wreak havoc on your organization. Intercept X with XDR includes anti-ransomware technology that detects malicious encryption processes and shuts them down before they can spread across your network. It prevents both file-based and master boot record ransomware.
Any files that were encrypted are rolled back to a safe state, meaning your employees can continue working uninterrupted, with minimal impact to business continuity. You get detailed post-cleanup information, so you can see where the threat got in, what it touched, and when it was blocked.
The first EDR designed for security analysts and IT administrators
Intercept X Advanced with EDR allows you to ask any question about what has happened in the past, and what is happening now on your endpoints. Hunt threats to detect active adversaries, or leverage for IT operations to maintain IT security hygiene. When an issue is found remotely respond with precision. By starting with the strongest protection, Intercept X stops breaches before they start. It cuts down the number of items to investigate and saves you time.
Intercept X Advanced with XDR is the industry’s only XDR solution that synchronizes native endpoint, server, firewall, email, cloud and O365 security. Get a holistic view of your organization’s environment with the richest data set and deep analysis for threat detection, investigation and response for both dedicated SOC teams and IT admins.
Sophos Intercept X is the industry leading Endpoint Security solution that reduces the attack surface and prevents attacks from running. Combining anti-exploit, anti-ransomware, deep learning AI and control technology it stops attacks before they impact your systems. Intercept X uses a comprehensive, defense in depth approach to endpoint protection, rather than relying on one primary security technique.
Achieve unmatched endpoint threat prevention. Intercept X uses deep learning, an advanced form of machine learning to detect both known and unknown malware without relying on signatures.
Deep learning makes Intercept X smarter, more scalable, and more effective against never-seen-before threats. Intercept X leverages deep learning to outperform endpoint security solutions that use traditional machine learning or signature-based detection alone.
Block ransomware attacks before they wreak havoc on your organization. Intercept X with XDR includes anti-ransomware technology that detects malicious encryption processes and shuts them down before they can spread across your network. It prevents both file-based and master boot record ransomware.
Any files that were encrypted are rolled back to a safe state, meaning your employees can continue working uninterrupted, with minimal impact to business continuity. You get detailed post-cleanup information, so you can see where the threat got in, what it touched, and when it was blocked.
The first EDR designed for security analysts and IT administrators
Intercept X Advanced with EDR allows you to ask any question about what has happened in the past, and what is happening now on your endpoints. Hunt threats to detect active adversaries, or leverage for IT operations to maintain IT security hygiene. When an issue is found remotely respond with precision. By starting with the strongest protection, Intercept X stops breaches before they start. It cuts down the number of items to investigate and saves you time.
Intercept X Advanced with XDR is the industry’s only XDR solution that synchronizes native endpoint, server, firewall, email, cloud and O365 security. Get a holistic view of your organization’s environment with the richest data set and deep analysis for threat detection, investigation and response for both dedicated SOC teams and IT admins.
With “Sophos Central MDR” you can achieve the highest level of security Sophos can currently offer for the protection of your endpoints (macOS 10.15+, Windows 8.1+). In this bundle, you get all the features of Intercept X Advanced with XDR and the new, enhanced MDR service.
With the MDR service, Sophos provides a highly available “Service Operation Center” (SOC). It is the perfect complement for all IT administrators where there are no free resources to go threat hunting themselves with XDR's tools. It takes highly skilled and specialized personnel to use XDR to proactively scan the network for potential threats and take the correct steps when an attack occurs.
With Sophos Central MDR for Server, you no longer need to look for trained personnel yourself. Sophos provides a team of experts who work 24/7 to combat threats.
If something has been detected on your system that could not be fixed automatically and requires human expertise, the MDR team is there for you on a 24/7 basis. An expert then takes a close look at the critical note and uses his experience to decide what needs to be done.
The MDR team pays special attention to attacks executed through legitimate processes, such as PowerShell. Such attacks are often successful because they are difficult for monitoring tools to detect. The MDR team uses proprietary analytics to monitor these processes to ensure they are not being misused for malicious purposes.
The Security Health Check ensures that your Sophos Central products can always operate at maximum performance. To do this, the MDR team looks at your network requirements and makes recommendations for configuration changes.
You will learn the current state of your systems, what intelligence was gathered during the reporting period, and what threats were averted. A histogram of these reports is then created over the period where you use the MDR service. With the help of this data, Sophos creates so-called "scorecards", with which one can compare oneself to previous periods.
Regardless of whether you choose the normal MDR or MDR Complete variant, you retain control over how autonomously the MDR team should operate. This is regulated right at the beginning in the so-called onboarding process. When you purchase the Sophos MDR service, you can choose from three options that determine what response you expect from the MDR team:
With “Sophos Central MDR” you can achieve the highest level of security Sophos can currently offer for the protection of your endpoints (macOS 10.15+, Windows 8.1+). In this bundle, you get all the features of Intercept X Advanced with XDR and the new, enhanced MDR service.
With the MDR service, Sophos provides a highly available “Service Operation Center” (SOC). It is the perfect complement for all IT administrators where there are no free resources to go threat hunting themselves with XDR's tools. It takes highly skilled and specialized personnel to use XDR to proactively scan the network for potential threats and take the correct steps when an attack occurs.
With Sophos Central MDR for Server, you no longer need to look for trained personnel yourself. Sophos provides a team of experts who work 24/7 to combat threats.
If something has been detected on your system that could not be fixed automatically and requires human expertise, the MDR team is there for you on a 24/7 basis. An expert then takes a close look at the critical note and uses his experience to decide what needs to be done.
The MDR team pays special attention to attacks executed through legitimate processes, such as PowerShell. Such attacks are often successful because they are difficult for monitoring tools to detect. The MDR team uses proprietary analytics to monitor these processes to ensure they are not being misused for malicious purposes.
The Security Health Check ensures that your Sophos Central products can always operate at maximum performance. To do this, the MDR team looks at your network requirements and makes recommendations for configuration changes.
You will learn the current state of your systems, what intelligence was gathered during the reporting period, and what threats were averted. A histogram of these reports is then created over the period where you use the MDR service. With the help of this data, Sophos creates so-called "scorecards", with which one can compare oneself to previous periods.
Regardless of whether you choose the normal MDR or MDR Complete variant, you retain control over how autonomously the MDR team should operate. This is regulated right at the beginning in the so-called onboarding process. When you purchase the Sophos MDR service, you can choose from three options that determine what response you expect from the MDR team: