Technical Specifications
Compare the feature set of Sophos’s various endpoint products to protect your clients. Not sure which protection best suits your business? We advise you free of charge and completely without obligation.

Microsoft has unveiled the new Surface Pro 9, a new tablet that
retains the traditional design as its predecessor but with new internals and
the choice of the ARM processor or the more powerful 12th Gen Intel silicon.
Similar to the Surface Pro 8, the Surface Pro 9 has a unibody made
with aluminum, a 13-inch screen (3:2 aspect ratio), and a 120Hz refresh rate.
You have the choice of an Intel 12th Gen Core i7 or i5 processor, and this
time, you can also get the tablet with a Microsoft SQ3 processor powered by
Qualcomm Snapdragon. In addition, depending on the model, the Surface Pro 9
comes with up to 32GB of DDR5 memory, up to 1TB of replaceable storage, and 5G
connectivity.
As for performance, the company claims up to 50
percent more performance from the Intel model than the Surface Pro 8, and the
two Thunderbolt 4 ports provide super-faster data transfer and the ability to
drive two 4K external monitors or use external GPUs. Also, you can get up to
15.5 hours of battery life and up to 19 hours with the ARM-based model.
Color options for
the Pro 9 include Platinum, Graphite, Sapphire, and Forest, but the color
availability will depend on the model you choose. Of course, the
detachable keyboard and Slim Pen are sold separately.
Also, as part of the 10-year anniversary of
Surface, Microsoft is partnering with London-based global design house
“Liberty” to offer a special-edition Surface Pro keyboard and laser-etched
Surface Pro 9 with an exclusive pattern in a vibrant blue floral inspired by
the Windows 11 Bloom wallpaper.
The Surface Pro 9 pricing starts at $1000 and can go up
to $2600 for the Intel Core i7 model. The ARM-based model starts at $1300 and
can go up to $1900 with a maxed-out configuration. The tablet is available
starting October 25, 2022, and you can pre-order from the technologysurface.com
Acrobat Standard includes basic PDF features, such as: Edit and organize PDFs. Convert documents to and from PDF. Fill out forms, sign documents, and request e-signatures. Password-protect files.
You get everything your organization needs to design standout experiences, including 20+ Creative Cloud desktop and mobile apps, built-in templates, cloud services, and exclusive business features.
Adobe offers two forms of Adobe VIP subscriptions: Teams licensing and Enterprise licensing. While the user experience of the product features stays the same for both Teams and Enterprise, the benefits of moving to Enterprise – from an administrator's point of view – make the move valuable.
Yes, Adobe Acrobat can be used for both personal and commercial purposes. However, it is important to ensure that you are using the software in compliance with Adobe's licensing terms and conditions.
Sophos Central Intercept X Advanced is a combination of Sophos Central Endpoint Protection and Intercept X products.
With Sophos Central Intercept X Advanced, you get all the features of Sophos Central Endpoint Protection and Intercept X in one product.
On the one hand, you benefit from great functions such as "Peripheral Control" or "Malicious Traffic Detection", and at the same time you get a specialist on your computer with Intercept X, which uses a technology called "CryptoGuard" to detect as soon as malware tries to encrypt files on your computer and stops this process immediately. Files that have already been encrypted are then automatically restored, so there is no data loss.
Would you like to see the Sophos Central user interface live? Just go to central.sophos.com and use the demo account. Username: demo@sophos.com / Password: Demo@sophos.com
Preventing the exploitation of security vulnerabilities.
Sophos Exploit Protection is a unique technology in Intercept X that prevents previously unknown or unpatched vulnerabilities in applications or operating system components from being exploited. With Intercept X, every application is monitored in the background and every action is checked to see if an exploit technique is being attempted.
If such a technique is detected, Exploit Prevention prevents a vulnerability from being exploited and restores the system to a secure state.
Find out the cause of the attack.
Imagine that, despite all the protective measures, malware has made it into your network. How could this happen? Thanks to the root cause analysis in Intercept X, this mystery can be uncovered with an impressive 360-degree analysis. The Root Cause Analysis Tool can tell you in great detail how the malware got into your network, which devices were infected and what steps you should take now.
With root cause analysis, you'll never be in the dark again if your network has been infected by an unknown malware.
Restores the system to its original state after an attack.
With Intercept X, thanks to technologies like CryptoGuard, you are protected against signatureless malware, such as ransomware, but after an attempted attack, your system still needs to be cleaned of all remnants. Since there is no cleaning routine for unknown malware, the entire processes of the executed malware must be forensically examined. This task is performed by Sophos Clean.
Sophos Clean performs a complete cleaning of the system after an attack has been stopped. It not only removes the malware itself, but replaces infected Windows resources with more secure original versions and ultimately restores the system to its original state, as it was before the infection.
Compare the feature set of Sophos’s various endpoint products to protect your clients. Not sure which protection best suits your business? We advise you free of charge and completely without obligation.
McAfee MVISION Endpoint 1 McAfee MVISION Endpoint Advanced endpoint security for Microsoft Windows 10 Organizations looking for simpler, more affordable alternatives to full-featured endpoint security platforms (EPP) are embracing native security like Windows Defender. While Defender provides essential base-level protection, it’s still necessary to apply advanced countermeasures like machine learning to mount a complete defense against sophisticated fileless and zero-day malware-based threats. The key to success lies within leveraging, strengthening, and managing the security already built into Windows 10 without introducing the complexity of multiple consoles. Connect With Us Security or Complexity? Because these tools are usually managed separately, security teams are faced with the dilemma of whether to get a stronger defense at the cost of adding complexity. Typically, this also means eliminating the financial and operational savings they had hoped to gain. A better choice: advanced defenses and cohesive management With McAfee® MVISION Endpoint, you can eliminate the dilemma of effectiveness or efficiency by getting both. You get file, fileless, and behavioral machine learning analysis for advanced threat detection and centralized management for every endpoint in your environment. You can also avoid complex workflows, thanks to a consistent and centralized console for policy management of Windows Defender, Windows Firewall, McAfee defenses, and Mac or Linux systems. Comanagement not only removes redundant entry time, it improves your visibility into your endpoint environment. Maximize your defenses McAfee MVISION Endpoint delivers enhanced detection and correction capabilities to augment native controls, which are always up to date. Machine learning, credential theft monitoring, and rollback remediation substantially boost the basic security built into the Windows 10 operating system (OS) and effectively combat advanced, zero-day threats. This approach lets you avoid the tricky questions of whether to invest in native or third-party technologies by aligning and giving you the best of both.
Recover time McAfee machine learning technology offers a much higher detection rate than signature-based defenses alone, with fewer false positives than competing solutions. This helps keep administrators focused on the real threats in their environments, rather than on exonerating the non-malicious. McAfee MVISION Endpoint is also able to monitor and restore the original versions of files impacted by suspicious processes and to remove other malicious files or processes that may have been introduced. For users, this means they remain productive rather than dealing with downtime during remediation and recovery. For administrators, that means less time spent on re-imaging or recovering compromised endpoints and more time spent on making their organization productive. Get more visibility McAfee MVISION Endpoint is managed using a single pane of glass that gives visibility into your environment for both threats and compliance. Instead of pivoting from one console to another to connect the dots on what, where, and how a threat event happened, an easyto-use dashboard and configurable alerts guide you to the data that is most important. Management flexibility McAfee MVISION Endpoint offers a choice of: ■ Pure SaaS Management: Multitenant, globally scaled, and maintained by McAfee. − Benefits: Anytime, anywhere access to the management console, automatic updates, and management maintenance for a lower total cost of ownership (TCO). ■ Virtual deployment: Fully operational in less than an hour with management deployed in an Amazon Web Services (AWS) environment. − Benefits: Leverage existing investments in virtualized environments to lower your deployment and maintenance costs while retaining customized control. ■ Local deployment: An on-site, locally installed deployment of the management software on a server. − Benefits: Customers can use existing deployments and manage multiple McAfee technologies centrally
ESET Secure Authentication provides powerful software-based two-factor authentication (2FA), safeguarding your company’s mobile workforce against data breaches due to compromised passwords and aiding in regulatory compliance with HIPAA, PCI DSS and NIST. ESET Secure Authentication validates each VPN and Outlook Web Access (OWA) login with a unique one-time-password (OTP) adding an important layer of security to your company’s sensitive data. Simple to manage, ESET Secure Authentication is more flexible, cost effective, and easy to use than hardware OTP tokens or appliances.
ESET Secure Authentication helps businesses access their data securely. Our solution utilizes the existing Active Directory domain, allowing you to set up ESET’s two-factor authentication in just 10 minutes – and thus easily reduce the risk of data breaches, caused by stolen, weak or compromised passwords.
The solution consists of the server side and the client side – the latter comes in the form of a mobile app. The authentication options include Push Authentication, as well as generation and delivery one-time passwords (OTPs) via the mobile app, but also via SMS messages or your organization’s existing hardware tokens.
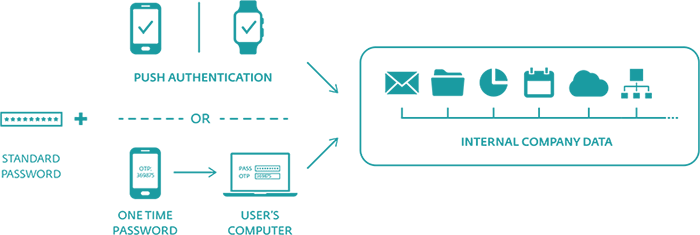
ESET Secure Authentication helps you secure your data in a hassle-free way. By complementing your normal authentication with a second factor, it effectively reduces the risk of data breaches caused by weak or leaked passwords.
Use ESET Secure Authentication to protect:
Easy integration with your RADIUS-based services or via an API to your existing Active Directory-based authentication. Non Active Directory customers with custom systems can use the easy-to-deploy SDK.
On-premises license package for anti-virus, web security with firewall and USB device control
Trend Micro Worry-Free Standard is easy to install and easy to use. Because it is specially designed for small businesses, no IT skills are required. Centralized visibility and control gives you an overview of what is going on in your company. In addition, complete protection is guaranteed with minimal impact on system performance.
Always one step ahead of threats
Proactively stop threats before they reach your business with cloud-based protection from the Trend Micro ™ Smart Protection Network ™. By leveraging the latest global threat intelligence, your devices have access to the latest threat intelligence.
The number of small businesses falling victim to cybercriminal data theft schemes is on the rise. These criminals are known for using a variety of techniques, such as ransomware, spam, malware, phishing, and advanced targeted attacks—custom built to bypass traditional antimalware solutions.
Trend Micro™ Worry-Free™ Business Security, powered by XGen™ security, provides complete user protection that includes antivirus, antispam, web security, ransomware protection, and data security for your PCs, Macs and servers.
Worry-Free Business Security is easy to use, has a small footprint, and won’t slow you or your staff down. With this solution, you can be confident that your IT security is comprehensive and your business’ data is safe.
Using global threat intelligence from Trend Micro™ Smart Protection Network™, Worry-Free Business Security provides immediate protection against the latest threats. Every day, Smart Protection Network analyzes more than 15 terabytes of threat data, to which it then identifies and blocks 250+ million threats in the cloud before they can reach your systems.
What is XGen™ Security?
Trend Micro Worry-Free, powered by XGen™ security is the first to infuse high-fidelity machine learning that uniquely analyzes files before execution and during runtime, for more accurate detection without false positives.
eScan Total Security Suite (Cyber Vaccine Edition) delivers complete protection for your devices. It is packed with the largest threat-detection network, virus protection, and home network security that won’t slow down your PC. New cloud protection technology detects threats as they emerge in real-time, Dynamic Proactive Behavioral Analysis Engine protects you even when offline, and our custom-built secure browser delivers top security and tough protection when shopping and making payments online. There is sophisticated layered real-time protection that monitors the computer against malware, keeping your application and data safe.
Our powerful scan engine provides security against known and unknown malware, phishing, and virus attacks in real-time. eScan TSS is equipped with futuristic technologies like Proactive Behavioral Analysis Engine (PBAE), Non-Intrusive Learning Pattern (NILP), MicroWorld Winsock Layer (MWL) and many more. Smart parental control protects your kids from online threats and unwanted content.
ZWCAD is a fast and powerful 2D CAD solution that offers unparalleled compatibility with AutoCAD®3. It empowers architects, engineers, and designers in the AEC and manufacturing industries to effortlessly bring their creative visions to life.
Choose from one of three pen tips with the right feel for you. Stay with the medium tip to get the feel of a pencil or swap it with a low-friction tip similar to a fine-point pen.
Empower all-day impact with tablet portability and laptop
performance with our most powerful Pro. Surface Pro 9 helps keep teams
connected with optional 5G,18 enables work on their terms
with built-in security, and the power they need to succeed.
Whether you’re still invested in Windows 10 or are
ready to introduce Windows 11 to your workforce, you have choices. Both options
are available for Surface Pro 8.
More than five million organisations around the world rely on Acrobat to create and edit PDFs, convert them to Microsoft Office formats and so much more. When you’re working remotely and need tools that empower collaboration and help keep business moving, use Acrobat — and make it happen.
Get it done with all‑in‑one PDF tools and easy e‑signatures in Adobe Acrobat Pro. Effortlessly request, track, and collect signatures in a few clicks.
Important note: A named license means that you can assign it to a “user”. That user can access the license on any device they wish to use it from i.e. a laptop or a desktop (to a maximum of 2 devices).
Top features | Acrobat Pro for teams | Acrobat Pro for enterprise |
Edit text and images, reorder and delete pages in a PDF | ||
Convert PDFs and export to Word, Excel, and PowerPoint | ||
Sign documents, request e-signatures and track responses in real time | ||
Integrate with enterprise applications, including Microsoft 365 and SharePoint | ||
Reassign licences in the web-based Admin Console | ||
Redact to permanently remove sensitive visible information in PDFs | ||
Collect e-signatures from anyone that fills in a web form | ||
Add a logo to brand your agreements and upload existing PDF forms to instantly create web forms | ||
Deploy with named users based on Federated ID, Enterprise ID | Adobe ID only | |
Access advanced 24/7 tech support |
Endpoint Encryption by ESET is a simple-to-use encryption application for companies large and small. Take advantage of the optimized setup that speeds up the time to adoption for admins. The client side requires minimal user interaction, increasing user compliance and the security of your company data.
Do you do business in the European Union? The EU's General Data Protection Regulation (GDPR) comes into force in May 2018, and introduces significant new penalties for organizations that fail to protect their users' data adequately. One proven solution for data protection is encryption.
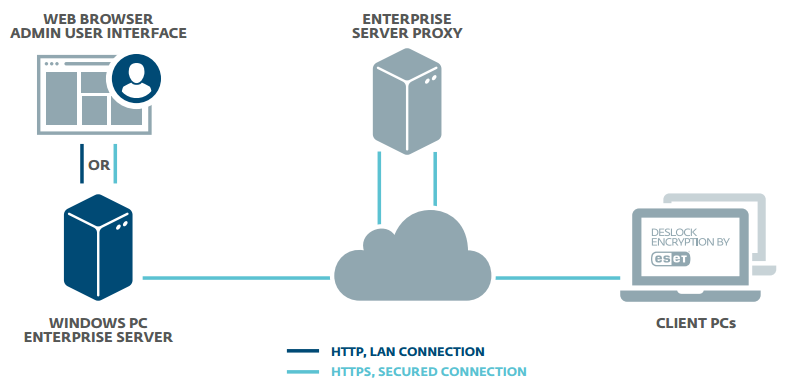
Data is a critical part of every organization, but this most valuable asset often poses a huge risk when it travels or is transmitted beyond the corporate network. Full disk and removable media encryption protect laptop computers against the unexpected. File, folder and email encryption allow fully secure collaboration across complex workgroups and team boundaries, with security policy enforced at all endpoints by the Endpoint Encryption+ Enterprise Server. Meet your data security compliance obligations with a single MSI package.
The Endpoint Encryption+ Enterprise server can manage users and workstations together or independently. Activation, and changes to security policy, software feature-set, encryption keys and endpoint status are all handled, securely through the cloud keeping your most high-risk endpoints under close control at all times Home and mobile working make extending encryption security policy beyond the perimeter of your network a necessity. Only Endpoint Encryption+ offers full control wherever your users are.
Your business holds sensitive data that must be kept safe, which is why we do more than just protect every endpoint. Adaptive Security detects advanced threats, while server hardening enhances high-performance protection with additional application, web and device controls, to prevent the theft of corporate and financial information.
This tier includes all the functionality delivered by Kaspersky Endpoint Security for Business Select, plus additional advanced technologies that do even more to protect your business.
Identifies vulnerabilities and applies the latest patches to close attack entry-points, as well as letting you control which applications are allowed to run on your servers. Complemented by enterprise-grade web and device controls and a centralized security management console.
Endpoint detection and response capabilities that identify abnormal behavior, automatically detecting and remediating targeted ransomware and in particular fileless threats which try to mimic common behavior like PowerShell script execution.
Our Linux and Windows Server security has been developed specifically for application and terminal servers. Encryption functions – plus OS-embedded firewall and encryption management – guard corporate and customer information to help you achieve key compliance goals, including GDPR.
Automates software tasks including the creation, storage and cloning of system images – saving you time whenever you need to roll out new systems or update software on existing systems.
We’re pioneers in providing the highest levels of transparency and data sovereignty, as well as neutrality. We process core data in geopolitically neutral Switzerland, where our partners can review our source code.
We are recognized for innovation – and have identified more advanced threats than any other vendor. Whether your IT is on-site or outsourced, our security adapts to protect you from new threats.