Technical Specifications
Compare the range of functions of the different Server from Sophos to protect your infrastructure. Not sure which protection best suits your business? We can advise you free of charge and without any obligation.

Busy
Software basic edition has been especially designed thoroughly to cater small
business accounting needs. Small owners now can easily scale and manage their
accounting heads properly and effectively with its outpace features, it offers
financial accounting management like - Sale, Purchage,Payment,receipt,contra
etc.,inventory management various type of stock tracking-Mrp-wise stock
tracking,Date-wise stock tracking etc., billing/invoicing, etc
Busy
Software Basic Edition has some special key features which makes accounting
easy to work with BUSY basic edition we can do inventory management,
confugurable invoicing, financial accounting, GST reports view purpose, GST
& HSN validation, PDC entry and bank reconciliation.
BUSY basic
Edition has fully user definable access rights. we can also analyze sale/purchage,
mobile application, dynamic QR code, e-mail/SMS of vouchers & reports. we
can also manage sale /purchage, payment, receipt, contra , journal & all
financial entries.
An integrated bussing accounting and management solution, BUSY is a one-stop solution for your financial and payroll needs. It offers multi-location inventory, multi-currency support, order processing capabilities, and helps you make informed decisions. Moreover, it is best suited for the FMCG, retail, manufacturing, trading, and distribution businesses.
The Complete Business Accounting Software that has everything you need to grow your business to the next level. BUSY with its powerful bunch of features is helping businesses manage not just your accounts but other business processes as well, like Inventory / Invoicing / Taxation / Payroll & much more.
Add an extra layer of protection to your Microsoft 365 cloud email and OneDrive. Protect your company computers, laptops and mobiles with security products all managed via a cloud-based management console. The solution includes cloud sandboxing technology, preventing zero-day threats, and full disk encryption capability for enhanced data protection.
Does Oracle Database have more than one edition? Yes, I know it has been
like this for many years, but I think it is worth pointing this out again. When
looking at the Oracle Database - there are actually a few options available to
you. Some might not actually know this, as the only option they might be
presented with by default could be Oracle Enterprise Edition (EE). Don’t get me
wrong, it is an amazing solution with a plethora of options. But it does in
fact, as I always say, have a little brother – Oracle Standard Edition 2, which
actually is worth looking at. It might not have all the features - or bells and
whistles as some say; but it is feature-rich and at the core still, an amazing
database edition which if you look closely, it could be the right fit for you.
Oracle
Database Standard Edition 2 (SE2) can be licensed and used on servers with a
maximum capacity of 2 CPU sockets. There is no limit to the number of cores. It
is important to note though that Oracle Database Standard Edition 2
automatically limits the maximum number of CPU threads to 16 at any one time.
To some, this might be seen as a limitation, but for most this should be more
than sufficient to run workloads - especially if later faster CPU models are
used. One important thing when the initial version of Standard Edition 2 was
released was that it came bundled with Oracle Real Application Clusters (RAC).
This unfortunately has changed since Oracle released the 19c update. As of 19c,
Oracle Standard Edition 2 does not include the Oracle RAC option, which was a
big shock to most of us. However, since the release of SE2 and the limitations
on 16 threads using Oracle RAC with SE2 became a less attractive option, many
new installations of Oracle SE2 tend to be more single instance than Oracle RAC.
Plenty of companies that still had the Oracle Standard Edition (SE) option
(usually running 11.2.0.4 database patched version) which allowed up to 4 CPU
sockets with no thread limitation, started looking at keeping this more long
term. Short term this might seem like a good plan while you review the options
going forward. It is recommended to make sure you have a support agreement in
place - and always keep an eye on this Oracle support note: Release Schedule of
Current Database Releases (Doc ID 742060.1).
This proprietary VGA adapter lets you share photos, video, and presentations in a way that's larger than life. Plug into VGA-compatible displays, monitors, or projectors. Compatible with your Surface with USB-C port.
Protect your company computers, laptops and mobiles with cutting-edge security products all managed via a cloud-based management console.
Central Managed Detection and Response Complete Server is Sophos' most flexible and comprehensive 24/7 managed threat protection, detection, and response service. MDR Complete provides analyst-led threat hunting and investigation as well as full-scale incident response. Threats are fully eliminated. Sophos MDR Complete includes support for 3rd party server protection solutions. Optional add-ons can be purchased for Sophos Network Detection and Response (NDR), Sophos 3rd party integration packs, and extended data storage. For licensing clarity, Central Managed Detection and Response includes Central Intercept X Advanced with XDR as well as 3rd party endpoint compatibility.
The need for always-on security operations has become an imperative. However, the complexity of modern operating environments and the velocity of cyberthreats make it increasingly difficult for most organizations to successfully manage detection and response on their own.
With Sophos MDR, our expert team stops advanced human-led attacks. We take action to neutralize threats before they can disrupt your business operations or compromise your sensitive data. Sophos MDR is customizable with different service tiers, and can be delivered via our proprietary technology or using your existing cybersecurity technology investments.
Enabled by extended detection and response (XDR) capabilities that provide complete security coverage wherever your data reside, Sophos MDR can:
ESET PROTECT ENTRY On-Prem features
A. ESET ENDPOINT SECURITY
Antivirus and Antispyware
Eliminates all types of threats, including viruses, rootkits, worms and spyware
Optional cloud-powered scanning:
Whitelisting of safe files based on file reputation database in the cloud for better detection and faster scanning. Only information about executable and archive files is sent to the cloud – such data are not personally attributable.
Virtualization Support
ESET Shared Local Cache stores metadata about already scanned files within the virtual environment so identical files are not scanned again, resulting in boosted scan speed.
ESET module updates and virus signatures database are stored outside of the default location, so these don’t have to be downloaded every time a virtual machine is reverted to default snapshot.
Host-Based Intrusion Prevention System (HIPS)
Enables you to define rules for system registry, processes, applications and files. Provides anti-tamper protection and detects threats based on system behavior.
Exploit Blocker
Strengthens security of applications such as web browsers, PDF readers, email clients or MS office components, which are commonly exploited.
Monitors process behaviors and looks for suspicious activities typical of exploits.
Strengthens protection against targeted attacks and previously unknown exploits, i.e. zero-day attacks that could be used by crypto-ransomware to enter the targeted system.
Advanced Memory Scanner
Monitors the behavior of malicious processes and scans them once they decloak in the memory. This allows for effective infection prevention, even from heavily obfuscated malware,
often detecting crypto-ransomware prior to it encrypting valuable files.
Client Antispam
Effectively filters out spam and scans all incoming emails for malware. Native support for Microsoft Outlook (POP3, IMAP, MAPI).
Cross-Platform Protection
ESET security solutions for Windows are capable of detecting Mac OS threats and vice-versa, delivering better protection in multi-platform environments.
Web Control
Limits website access by category, e.g. gaming, social networking, shopping and others. Enables you to create rules for user groups to comply with your company policies.
Soft blocking – notifies the end user that the website is blocked giving him an option to access the website, with activity logged.
Anti-Phishing
Protects end users from attempts by fake websites to acquire sensitive information such as usernames, passwords or banking and credit card details.
Two-Way Firewall
Prevents unauthorized access to your company network. Provides anti-hacker protection and data exposure prevention. Lets you define trusted networks, making all other connections, such as to
public Wi-Fi, in ‘strict’ mode by default. Troubleshooting wizard guides you through a set of questions, identifying problematic rules, or allowing you to create new ones.
Vulnerability Shield
Improves detection of Common Vulnerabilities and Exposures (CVEs) on widely used protocols such as SMB, RPC and RDP.
Protects against vulnerabilities for which a patch has not yet been released or deployed.
Botnet Protection
Protects against infiltration by botnet malware – preventing spam and network attacks launched from the endpoint.
Device Control
Blocks unauthorized devices (CDs/DVDs and USBs) from your system. Enables you to create rules for
user groups to comply with your company policies. Soft blocking – notifies the end user that his device is blocked and gives him the option to access the device, with activity logged.
Idle-State Scanner
Aids system performance by performing a full scan proactively when the computer is not in use. Helps speed up subsequent scans by populating the local cache.
First Scan after Installation
Provides the option to automatically run low priority on-demand scan 20 minutes after installation, assuring protection from the outset.
Update Rollback
Lets you revert to a previous version of protection modules and virus signature database.
Allows you to freeze updates as desired - opt for temporary rollback or delay until manually changed.
Postponed Updates
Provides the option to download from three specialized update servers: pre-release (beta users), regular release (recommended for non-critical systems) and postponed release (recommended for company- critical systems – approximately 12 hours after regular release).
Local Update Server
Saves company bandwidth by downloading updates only once, to a local mirror server.
Mobile workforce updates directly from ESET Update Server when the local mirror is not available. Secured (HTTPS) communication channel is supported.
RIP & Replace
Other security software is detected and uninstalled during installation of ESET Endpoint solutions. Supports both 32 and 64-bit systems.
Customizable GUI Visibility
Visibility of Graphical User Interface (GUI) to end user can be set to: Full, Minimal, Manual or Silent. Presence of ESET solution can be made completely invisible to end user, including no tray icon or notification windows.
By hiding the GUI completely, the “egui.exe” process does not run at all, resulting in even lower system resource consumption by the ESET solution.
ESET License Administrator
Makes it possible to handle all licenses transparently, from one place via web browser. You can merge, delegate and manage all licenses centrally in real-time, even if you are not using ESET Remote Administrator.
Touchscreen Support
Supports touch screens and high-resolution displays.
More padding for and complete rearrangement of GUI elements. Basic frequently used actions accessible from tray menu.
Low System Demands
Delivers proven protection while leaving more system resources for programs that end users regularly run. Can be deployed on older machines without the need for an upgrade, thereby extending hardware lifetime. Conserves battery life for laptops that are away from the office, using battery mode.
Right-to-Left Language Support
Native right-to-left language support (e.g. for Arabic) for optimum usability.
Remote Management
ESET Endpoint solutions are fully manageable via ESET Remote Administrator.
Deploy, run tasks, set up policies, collect logs, and get notifications and an overall security overview of your network – all via a single web-based management console.
Explore our award-winning security features that provide complete protection against today’s dynamic threats for all your devices. Security and Privacy – For you and your family!
Get real time, easy-to-understand visual snapshots of your digital wellbeing reports, along with recommendations to improve your digital safety and online privacy.
With "Sophos Central MDR for Server" you can achieve the highest level of security Sophos can currently offer for the protection of your Server (Linux, Windows Server 2008 R2+). In this bundle, you get all the features of Intercept X Advanced for Server with XDR and the new, enhanced MDR service.
With the MDR service, Sophos provides a highly available “Service Operation Center” (SOC). It is the perfect complement for all IT administrators where there are no free resources to go threat hunting themselves with XDR's tools. It takes highly skilled and specialized personnel to use XDR to proactively scan the network for potential threats and take the correct steps when an attack occurs.
With Sophos Central MDR for Server, you no longer need to look for trained personnel yourself. Sophos provides a team of experts who work 24/7 to combat threats.
If something has been detected on your system that could not be fixed automatically and requires human expertise, the MDR team is there for you on a 24/7 basis. An expert then takes a close look at the critical note and uses his experience to decide what needs to be done.
The MDR team pays special attention to attacks executed through legitimate processes, such as PowerShell. Such attacks are often successful because they are difficult for monitoring tools to detect. The MDR team uses proprietary analytics to monitor these processes to ensure they are not being misused for malicious purposes.
The Security Health Check ensures that your Sophos Central products can always operate at maximum performance. To do this, the MDR team looks at your network requirements and makes recommendations for configuration changes.
Seqrite Endpoint Security for Business software or Seqrite EPS is designed to keep your network and devices safe from cyber threats. Whether you run a big or small business, Seqrite has everything you need to protect your data and network. The software allows businesses of all sizes to have the essential tools for comprehensive data protection and network security.
Furthermore, the endpoint security software offers a wide range of features, including advanced endpoint protection, vulnerability scanning, asset management, IDS/IPS protection, and internet security.
Additionally, it excels in vulnerability scanning and patch management to help businesses identify and rectify application vulnerabilities and strengthen their security posture. With the increasing threat of ransomware, it is even more critical now to ensure complete network protection with Seqrite EPS. It addresses and prevents the most sophisticated cyber threats from entering your network and compromising data security.
Seqrite Endpoint Security for Business offers comprehensive and advanced features to safeguard your enterprise. With its multi-layered protection approach, including antivirus, anti-ransomware, firewall, and advanced device control, Seqrite EPS ensures comprehensive security. Its centralized administration, SIEM integration, and vulnerability scanning further ensure that you have complete visibility and control over your network.
Seqrite's indigenous scan engine and patented detection technologies keep you updated about potential threats, while the Endpoint Detection and Response (EDR) capabilities detect and report vulnerabilities. With seamless integration and user-friendly features, Seqrite Endpoint Security is the trusted choice for businesses seeking complete data protection.
K7 Total Security is a powerful antivirus software that helps protect your digital world from various online threats. With its comprehensive features and advanced technologies, it offers reliable protection against viruses, malware, spyware, ransomware, and other malicious attacks. This 1 User 1 Year license is designed to keep your devices safe and secure, allowing you to browse, shop, and work online with confidence for 1 year.
K7 Total Security is a comprehensive security solution that offers robust protection against viruses, malware, and other online threats. With its advanced features, it ensures that your digital life remains safe and secure. Here are some reasons to choose K7 Total Security:
With Sophos Central Intercept X for servers with XDR, you equip your servers with the maximum protection Sophos has to offer for servers. It includes all the functions of classic "Server Protection" with "Intercept X" for protection against ransomware and exploits, allowing you to protect your server environment against encryption Trojans. As the name of the product suggests, you also buy the "XDR" function.
XDR means "Extended Detection and Response" and is interesting for all those who want to get to the bottom of the cause of an attack in more detail, or in certain companies also have to. XDR is used, for example, when malware has been blocked or an exploit has been prevented. It could be that a thwarted attack is just a harbinger of a much larger attack. In our view, XDR can be seen as an extension of the "root cause analysis" already included in Intercept X, simply with many more options.
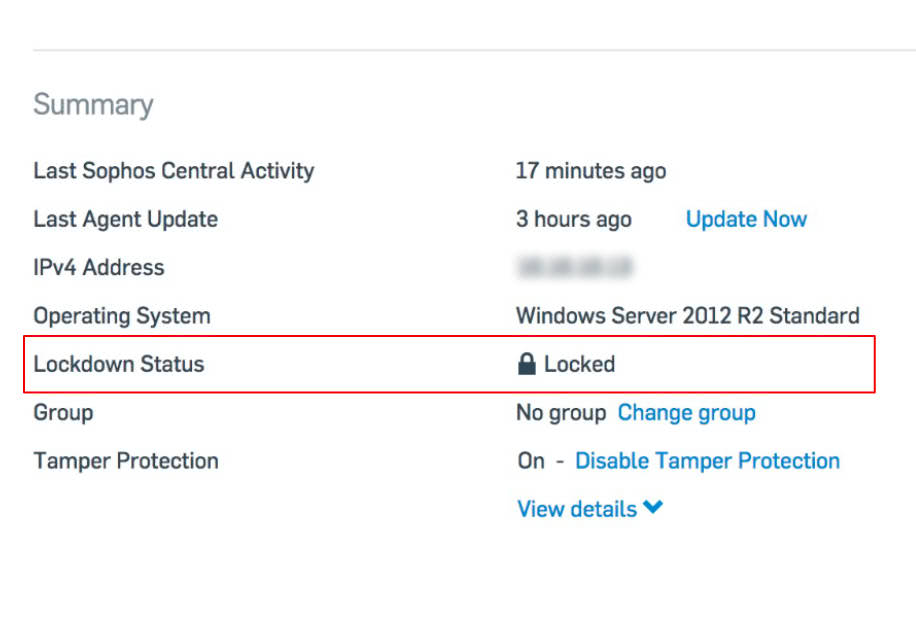
The Server lockdown gives you the benefit of one-click whitelisting. Once you activate the lockdown for your Server, it will first check if the system is threat-free. After that, it is necessary to record the current state of your server and create the whitelisting. All this happens in the background and does not affect the availability of your server. After one or two hours, indexing is usually complete and the system is in lockdown mode. From this point on, no software, including malware, can be installed on the system.
After lockdown, you can define so-called "update applications". For example, an update of an ERP can be such an update application. Windows updates are already whitelisted automatically and are allowed to update system components of Windows.
A classic antivirus doesn't stand a chance against encryption Trojans such as Petya, WannaCry or Locky. With CryptoGuard you get a technology on your Server that detects as soon as a ransomware tries to encrypt files on your Server and stops this process immediately. Already encrypted files are automatically restored afterwards, so that no data loss occurs.
CryptoGuard is the ideal complement to classic virus detection and is included as an additional layer of protection in Sophos intercept X for Server.
Find out the cause of the attack.
Imagine that, despite all the protective measures, malware has made it into your network. How could this happen? Thanks to the root cause analysis in Intercept X, this mystery can be uncovered with an impressive 360-degree analysis. The Root Cause Analysis Tool can tell you in great detail how the malware got into your network, which devices were infected and what steps you should take now.
With root cause analysis, you'll never be in the dark again if your network has been infected by an unknown malware.
Preventing the exploitation of security vulnerabilities.
Sophos Exploit Protection is a unique technology in Intercept X that prevents previously unknown or unpatched vulnerabilities in applications or operating system components from being exploited. With Intercept X, every application is monitored in the background and every action is checked to see if an exploit technique is being attempted.
If such a technique is detected, Exploit Prevention prevents a vulnerability from being exploited and restores the system to a secure state.
Compare the range of functions of the different Server from Sophos to protect your infrastructure. Not sure which protection best suits your business? We can advise you free of charge and without any obligation.
Best-in-class endpoint protection against ransomware & zero-day threats. Cross-platform solution with easy-to-use cloud or on-premises management, server security, advanced threat defense and full disk encryption.