- 14% Off
McAfee Complete Data Protection—Advanced 1 McAfee Complete Data Protection—Advanced Comprehensive data protection anywhere, anytime Sensitive data is constantly at risk of loss, theft, and exposure. Many times, the data simply walks right out the front door on a laptop or USB device. Companies that suffer such a data loss risk serious consequences, including regulatory penalties, public disclosure, brand damage, customer distrust, and financial losses. The rapid proliferation of mobile devices with large storage capacities and often internet access is opening up even more channels for data loss or theft, so protecting sensitive, proprietary, and personally identifiable information must be a top priority. McAfee® Complete Data Protection—Advanced addresses all of these concerns and many more.
Data Loss Prevention for Greater Control Preventing data loss at the endpoint begins with improving visibility and control over your data, even when it is disguised. McAfee Complete Data Protection— Advanced enables you to implement and enforce company-wide security policies that regulate and restrict how your employees use and transfer sensitive data via common channels, such as email, IM, printing, and USB drives. It does not matter if they are in the office, at home, or on the move—you stay in contro
Enterprise-Grade Drive Encryption Secure your confidential data with an enterprise-grade security solution that is FIPS 140-2 and Common Criteria EAL2+ certified and accelerated with the Intel Advanced Encryption Standard—New Instructions (Intel AES-NI) set. McAfee Complete Data Protection—Advanced uses drive encryption combined with strong access control via two-factor pre-boot authentication to prevent unauthorized access to confidential data on endpoints, including desktops, virtual desktop infrastructure (VDI) workstations, laptops, USB drives, CD/DVDs, and more
Removable Media, File and Folder, and Cloud Storage Encryption Ensure that specific files and folders are always encrypted, regardless of where data is edited, copied, or saved. McAfee Complete Data Protection—Advanced features content encryption that automatically and transparently encrypts the files and folders you choose on the fly—before they move through your organization. You create and enforce central policies based on users and user groups for specific files and folders without user interaction
- 9% Off
Overview:
With McAfee Complete Endpoint Protection — Business, you can spend more time on your business and less time worrying about security. This highly affordable, all-in-one solution provides top-rated endpoint security for all the devices in your enterprise: PCs, Macs, Linux systems, servers, virtual systems, smartphones, and tablets. Quickly and easily layer in protection against today’s most advanced threats, including encryption to protect your valuable data, behavioral zero-day intrusion prevention against attacks, hardware-enhanced protection against low-level, stealthy malware, and email, web, and mobile security to block phishing and multistage attacks. Easy installation and unified management reduce setup and maintenance. You can respond faster than ever.
Complete protection — Today, antivirus alone isn’t enough to defend against sophisticated, stealthy malware and attacks. The highest scoring vendor in an NSS Labs comparative test of current defenses against evasion attacks, McAfee finds, fixes, and freezes malware fast with multiple layers of protection. Hardware-enhanced system protection below the OS, available only from McAfee, targets stealthy attacks like rootkits that burrow deep into the kernel. And strong encryption secures your vital confidential data and prevents unauthorized access to PCs, Macs, laptops, and removable media — transparently and without slowing system performance. Behavior and reputation systems integrate with the cloud-based McAfee Global Threat Intelligence to protect against emerging cyberthreats across all vectors — file, web, message, and network.
Complete simplicity — With as few as four clicks and in as little as 20 minutes, you can be up and running. Web-based single console management with McAfee ePolicy Orchestrator software makes it easy to manage policies across all protections and systems and get instant visibility into security health across your entire infrastructure. With new real-time management, you can ask questions and fix vulnerabilities or correct problems faster than ever before.
Complete performance — Are you looking for security that supports business instead of slowing it down? Complete Endpoint Protection — Business minimizes security’s impact on users with fewer, smarter scans and advanced memory management. These technologies optimize CPU and memory usage to make strong security transparent to users across all platforms.
Defend all your endpoint devices, from traditional desktops and laptops to storage servers and mobile devices, with the industry’s highest scoring protection. McAfee® Complete Endpoint Protection—Business suite, an affordable, all-in-one solution, includes encryption to protect your valuable data, behavioral zero-day intrusion prevention for insidious exploits, hardware-enhanced protection against stealthy malware, as well as email, web, and mobile security to block phishing and multistage attacks. Single-console, web-based management eases the day-to-day burden on your IT staff and empowers them to act fast when threats strike.
Make endpoint security painless for your users and IT. McAfee Complete Endpoint Protection—Business helps growing organizations get security right, from turnkey installation to rapid response. With one unified solution, you cover all the devices in your enterprise—PCs, Macs, Linux systems, servers, smartphones, and tablets. Reduce complexity, cut costs, and protect against rootkits, mobile malware, targeted web and email attacks, and persistent threats. You get powerful, efficient protection and straightforward management that’s available only from McAfee, the market leader in endpoint security.
Key Advantages
- Get fast, top-rated hardware-enhanced protection against today’s toughest and stealthiest threats.
- Unify management across all your endpoints, from virtual machines and servers to PCs and mobile devices.
- Act in real time to fix vulnerabilities and stop threats in their tracks.
- Secure confidential data on all devices and removable media while you share files securely.
- 10% Off
McAfee Complete Data Protection—Advanced 1 McAfee Complete Data Protection—Advanced Comprehensive data protection anywhere, anytime Sensitive data is constantly at risk of loss, theft, and exposure. Many times, the data simply walks right out the front door on a laptop or USB device. Companies that suffer such a data loss risk serious consequences, including regulatory penalties, public disclosure, brand damage, customer distrust, and financial losses. The rapid proliferation of mobile devices with large storage capacities and often internet access is opening up even more channels for data loss or theft, so protecting sensitive, proprietary, and personally identifiable information must be a top priority. McAfee® Complete Data Protection—Advanced addresses all of these concerns and many more
Data Loss Prevention for Greater Control Preventing data loss at the endpoint begins with improving visibility and control over your data, even when it is disguised. McAfee Complete Data Protection— Advanced enables you to implement and enforce company-wide security policies that regulate and restrict how your employees use and transfer sensitive data via common channels, such as email, IM, printing, and USB drives. It does not matter if they are in the office, at home, or on the move—you stay in control.
Enterprise-Grade Drive Encryption Secure your confidential data with an enterprise-grade security solution that is FIPS 140-2 and Common Criteria EAL2+ certified and accelerated with the Intel Advanced Encryption Standard—New Instructions (Intel AES-NI) set. McAfee Complete Data Protection—Advanced uses drive encryption combined with strong access control via two-factor pre-boot authentication to prevent unauthorized access to confidential data on endpoints, including desktops, virtual desktop infrastructure (VDI) workstations, laptops, USB drives, CD/DVDs, and more.
Removable Media, File and Folder, and Cloud Storage Encryption Ensure that specific files and folders are always encrypted, regardless of where data is edited, copied, or saved. McAfee Complete Data Protection—Advanced features content encryption that automatically and transparently encrypts the files and folders you choose on the fly—before they move through your organization. You create and enforce central policies based on users and user groups for specific files and folders without user interaction.
Centralized Security Management and Advanced Reporting Use the centralized McAfee ePO software console to implement and enforce mandatory, company-wide security policies that control how data is encrypted, monitored, and protected from loss. Centrally define, deploy, manage, and update security policies that encrypt, filter, monitor, and block unauthorized access to sensitive data.
Key Advantages ■ Gain control over your data by monitoring and regulating how employees use and transfer data via common channels, such as email, IM, printing, and USB drives—both in and away from the office. ■ Stop data loss initiated by sophisticated malware that hijacks sensitive and personal information. ■ Secure data when it’s stored on desktops, laptops, tablets, and in the cloud. ■ Manage Apple FileVault and Microsoft BitLocker native encryption on endpoints directly from MVISION ePO or McAfee ePO software. ■ Communicate with and take control of your endpoints at the hardware level—whether they are powered off, disabled, or encrypted—to halt desk-side visits and endless help desk calls due to security incidents, outbreaks, or forgotten encryption passwords. ■ Prove compliance with advanced reporting and auditing capabilities. Monitor events and generate detailed reports that show auditors and other stakeholders your compliance with internal and regulatory privacy requirements
- 21% Off
McAfee Complete Data Protection—Advanced 1 McAfee Complete Data Protection—Advanced Comprehensive data protection anywhere, anytime Sensitive data is constantly at risk of loss, theft, and exposure. Many times, the data simply walks right out the front door on a laptop or USB device. Companies that suffer such a data loss risk serious consequences, including regulatory penalties, public disclosure, brand damage, customer distrust, and financial losses. The rapid proliferation of mobile devices with large storage capacities and often internet access is opening up even more channels for data loss or theft, so protecting sensitive, proprietary, and personally identifiable information must be a top priority. McAfee® Complete Data Protection—Advanced addresses all of these concerns and many more
Data Loss Prevention for Greater Control Preventing data loss at the endpoint begins with improving visibility and control over your data, even when it is disguised. McAfee Complete Data Protection— Advanced enables you to implement and enforce company-wide security policies that regulate and restrict how your employees use and transfer sensitive data via common channels, such as email, IM, printing, and USB drives. It does not matter if they are in the office, at home, or on the move—you stay in control.
Enterprise-Grade Drive Encryption Secure your confidential data with an enterprise-grade security solution that is FIPS 140-2 and Common Criteria EAL2+ certified and accelerated with the Intel Advanced Encryption Standard—New Instructions (Intel AES-NI) set. McAfee Complete Data Protection—Advanced uses drive encryption combined with strong access control via two-factor pre-boot authentication to prevent unauthorized access to confidential data on endpoints, including desktops, virtual desktop infrastructure (VDI) workstations, laptops, USB drives, CD/DVDs, and more.
Removable Media, File and Folder, and Cloud Storage Encryption Ensure that specific files and folders are always encrypted, regardless of where data is edited, copied, or saved. McAfee Complete Data Protection—Advanced features content encryption that automatically and transparently encrypts the files and folders you choose on the fly—before they move through your organization. You create and enforce central policies based on users and user groups for specific files and folders without user interaction.
Centralized Security Management and Advanced Reporting Use the centralized McAfee ePO software console to implement and enforce mandatory, company-wide security policies that control how data is encrypted, monitored, and protected from loss. Centrally define, deploy, manage, and update security policies that encrypt, filter, monitor, and block unauthorized access to sensitive data.
Key Advantages ■ Gain control over your data by monitoring and regulating how employees use and transfer data via common channels, such as email, IM, printing, and USB drives—both in and away from the office. ■ Stop data loss initiated by sophisticated malware that hijacks sensitive and personal information. ■ Secure data when it’s stored on desktops, laptops, tablets, and in the cloud. ■ Manage Apple FileVault and Microsoft BitLocker native encryption on endpoints directly from MVISION ePO or McAfee ePO software. ■ Communicate with and take control of your endpoints at the hardware level—whether they are powered off, disabled, or encrypted—to halt desk-side visits and endless help desk calls due to security incidents, outbreaks, or forgotten encryption passwords. ■ Prove compliance with advanced reporting and auditing capabilities. Monitor events and generate detailed reports that show auditors and other stakeholders your compliance with internal and regulatory privacy requirements
- 14% Off
Best-in-class endpoint protection against ransomware & zero-day threats. Cross-platform solution with easy-to-use cloud or on-premises management, server security, advanced threat defense and full disk encryption.
- Flexible management options
- Ransomware & zero-day protection
- Top-rated multilayered security
- Cross-platform coverage for Windows, Mac & Linux
- Mobile protection for Android & iOS
- Aids compliance with data protection regulations.
- 23% Off
Best-in-class endpoint protection against ransomware & zero-day threats. Cross-platform solution with easy-to-use cloud or on-premises management, server security, advanced threat defense and full disk encryption.
- Flexible management options
- Ransomware & zero-day protection
- Top-rated multilayered security
- Cross-platform coverage for Windows, Mac & Linux
- Mobile protection for Android & iOS
- Aids compliance with data protection regulations.
- 31% Off
Add an extra layer of protection to your Microsoft 365 cloud email and OneDrive. Protect your company computers, laptops and mobiles with security products all managed via a cloud-based management console. The solution includes cloud sandboxing technology, preventing zero-day threats, and full disk encryption capability for enhanced data protection.
- Improved protection against ransomware and zero-day threats via cloud-based sandboxing technology.
- Helps comply with data regulation thanks to full disk encryption capabilities on Windows and macOS.
- Protection against disruption caused by email-based attacks and malware in Microsoft 365 cloud applications.
- Easily accessible ESET PROTECT console improves TCO of security management.
- Single-pane-of-glass remote management for visibility to threats, users and quarantined items.
- Company endpoints and mobiles are protected via advanced multilayered technology, including file server security, now with secure banking protection.
- 24% Off
Add an extra layer of protection to your Microsoft 365 cloud email and OneDrive. Protect your company computers, laptops and mobiles with security products all managed via a cloud-based management console. The solution includes cloud sandboxing technology, preventing zero-day threats, and full disk encryption capability for enhanced data protection.
- Improved protection against ransomware and zero-day threats via cloud-based sandboxing technology.
- Helps comply with data regulation thanks to full disk encryption capabilities on Windows and macOS.
- Protection against disruption caused by email-based attacks and malware in Microsoft 365 cloud applications.
- Easily accessible ESET PROTECT console improves TCO of security management.
- Single-pane-of-glass remote management for visibility to threats, users and quarantined items.
- Company endpoints and mobiles are protected via advanced multilayered technology, including file server security, now with secure banking protection.
- 25% Off
Add an extra layer of protection to your Microsoft 365 cloud email and OneDrive. Protect your company computers, laptops and mobiles with security products all managed via a cloud-based management console. The solution includes cloud sandboxing technology, preventing zero-day threats, and full disk encryption capability for enhanced data protection.
- Improved protection against ransomware and zero-day threats via cloud-based sandboxing technology.
- Helps comply with data regulation thanks to full disk encryption capabilities on Windows and macOS.
- Protection against disruption caused by email-based attacks and malware in Microsoft 365 cloud applications.
- Easily accessible ESET PROTECT console improves TCO of security management.
- Single-pane-of-glass remote management for visibility to threats, users and quarantined items.
- Company endpoints and mobiles are protected via advanced multilayered technology, including file server security, now with secure banking protection.
- 45% Off
Add an extra layer of protection to your Microsoft 365 cloud email and OneDrive. Protect your company computers, laptops and mobiles with security products all managed via a cloud-based management console. The solution includes cloud sandboxing technology, preventing zero-day threats, and full disk encryption capability for enhanced data protection.
- Improved protection against ransomware and zero-day threats via cloud-based sandboxing technology.
- Helps comply with data regulation thanks to full disk encryption capabilities on Windows and macOS.
- Protection against disruption caused by email-based attacks and malware in Microsoft 365 cloud applications.
- Easily accessible ESET PROTECT console improves TCO of security management.
- Single-pane-of-glass remote management for visibility to threats, users and quarantined items.
- Company endpoints and mobiles are protected via advanced multilayered technology, including file server security, now with secure banking protection.
- 30% Off
Protect your company computers, laptops and mobiles with cutting-edge security products all managed via a cloud-based management console.
- Easily accessible ESET PROTECT Cloud console improves the TCO of security management.
- Single-pane-of-glass remote management for visibility to threats, users and quarantined items.
- Company endpoints and mobiles protected via advanced multilayered technology, including file server security, now with secure intranet and banking protection.
- Best-in-class endpoint security, utilizing ESET´s verified layered approach (combining the best of all worlds: cloud-based reputation, machine learning, and deep behavioral inspection).
- Award-winning endpoint protection combines the latest Machine Learning techniques with decades of human expertise.
- 25% Off
Protect your company computers, laptops and mobiles with cutting-edge security products all managed via a cloud-based management console.
- Easily accessible ESET PROTECT Cloud console improves the TCO of security management.
- Single-pane-of-glass remote management for visibility to threats, users and quarantined items.
- Company endpoints and mobiles protected via advanced multilayered technology, including file server security, now with secure intranet and banking protection.
- Best-in-class endpoint security, utilizing ESET´s verified layered approach (combining the best of all worlds: cloud-based reputation, machine learning, and deep behavioral inspection).
- Award-winning endpoint protection combines the latest Machine Learning techniques with decades of human expertise.
- 15% Off
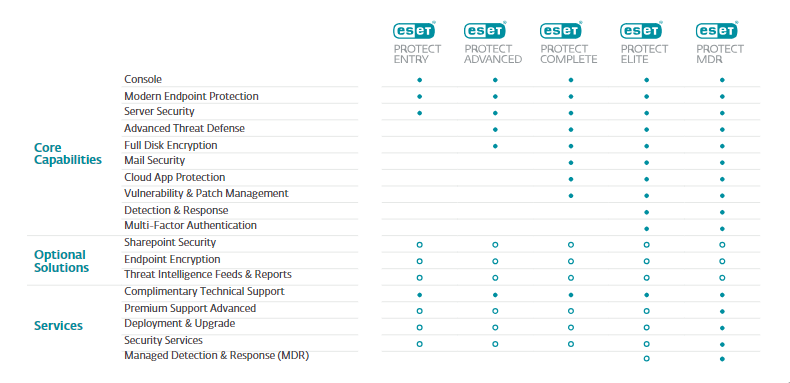
ESET PROTECT ENTRY On-Prem features
A. ESET ENDPOINT SECURITY
Antivirus and Antispyware
Eliminates all types of threats, including viruses, rootkits, worms and spyware
Optional cloud-powered scanning:
Whitelisting of safe files based on file reputation database in the cloud for better detection and faster scanning. Only information about executable and archive files is sent to the cloud – such data are not personally attributable.
Virtualization Support
ESET Shared Local Cache stores metadata about already scanned files within the virtual environment so identical files are not scanned again, resulting in boosted scan speed.
ESET module updates and virus signatures database are stored outside of the default location, so these don’t have to be downloaded every time a virtual machine is reverted to default snapshot.
Host-Based Intrusion Prevention System (HIPS)
Enables you to define rules for system registry, processes, applications and files. Provides anti-tamper protection and detects threats based on system behavior.
Exploit Blocker
Strengthens security of applications such as web browsers, PDF readers, email clients or MS office components, which are commonly exploited.
Monitors process behaviors and looks for suspicious activities typical of exploits.
Strengthens protection against targeted attacks and previously unknown exploits, i.e. zero-day attacks that could be used by crypto-ransomware to enter the targeted system.
Advanced Memory Scanner
Monitors the behavior of malicious processes and scans them once they decloak in the memory. This allows for effective infection prevention, even from heavily obfuscated malware,
often detecting crypto-ransomware prior to it encrypting valuable files.
Client Antispam
Effectively filters out spam and scans all incoming emails for malware. Native support for Microsoft Outlook (POP3, IMAP, MAPI).
Cross-Platform Protection
ESET security solutions for Windows are capable of detecting Mac OS threats and vice-versa, delivering better protection in multi-platform environments.
Web Control
Limits website access by category, e.g. gaming, social networking, shopping and others. Enables you to create rules for user groups to comply with your company policies.
Soft blocking – notifies the end user that the website is blocked giving him an option to access the website, with activity logged.
Anti-Phishing
Protects end users from attempts by fake websites to acquire sensitive information such as usernames, passwords or banking and credit card details.
Two-Way Firewall
Prevents unauthorized access to your company network. Provides anti-hacker protection and data exposure prevention. Lets you define trusted networks, making all other connections, such as to
public Wi-Fi, in ‘strict’ mode by default. Troubleshooting wizard guides you through a set of questions, identifying problematic rules, or allowing you to create new ones.
Vulnerability Shield
Improves detection of Common Vulnerabilities and Exposures (CVEs) on widely used protocols such as SMB, RPC and RDP.
Protects against vulnerabilities for which a patch has not yet been released or deployed.
Botnet Protection
Protects against infiltration by botnet malware – preventing spam and network attacks launched from the endpoint.
Device Control
Blocks unauthorized devices (CDs/DVDs and USBs) from your system. Enables you to create rules for
user groups to comply with your company policies. Soft blocking – notifies the end user that his device is blocked and gives him the option to access the device, with activity logged.
Idle-State Scanner
Aids system performance by performing a full scan proactively when the computer is not in use. Helps speed up subsequent scans by populating the local cache.
First Scan after Installation
Provides the option to automatically run low priority on-demand scan 20 minutes after installation, assuring protection from the outset.
Update Rollback
Lets you revert to a previous version of protection modules and virus signature database.
Allows you to freeze updates as desired - opt for temporary rollback or delay until manually changed.
Postponed Updates
Provides the option to download from three specialized update servers: pre-release (beta users), regular release (recommended for non-critical systems) and postponed release (recommended for company- critical systems – approximately 12 hours after regular release).
Local Update Server
Saves company bandwidth by downloading updates only once, to a local mirror server.
Mobile workforce updates directly from ESET Update Server when the local mirror is not available. Secured (HTTPS) communication channel is supported.
RIP & Replace
Other security software is detected and uninstalled during installation of ESET Endpoint solutions. Supports both 32 and 64-bit systems.
Customizable GUI Visibility
Visibility of Graphical User Interface (GUI) to end user can be set to: Full, Minimal, Manual or Silent. Presence of ESET solution can be made completely invisible to end user, including no tray icon or notification windows.
By hiding the GUI completely, the “egui.exe” process does not run at all, resulting in even lower system resource consumption by the ESET solution.
ESET License Administrator
Makes it possible to handle all licenses transparently, from one place via web browser. You can merge, delegate and manage all licenses centrally in real-time, even if you are not using ESET Remote Administrator.
Touchscreen Support
Supports touch screens and high-resolution displays.
More padding for and complete rearrangement of GUI elements. Basic frequently used actions accessible from tray menu.
Low System Demands
Delivers proven protection while leaving more system resources for programs that end users regularly run. Can be deployed on older machines without the need for an upgrade, thereby extending hardware lifetime. Conserves battery life for laptops that are away from the office, using battery mode.
Right-to-Left Language Support
Native right-to-left language support (e.g. for Arabic) for optimum usability.
Remote Management
ESET Endpoint solutions are fully manageable via ESET Remote Administrator.
Deploy, run tasks, set up policies, collect logs, and get notifications and an overall security overview of your network – all via a single web-based management console.
- 16% Off
ESET PROTECT ENTRY On-Prem features
A. ESET ENDPOINT SECURITY
Antivirus and Antispyware
Eliminates all types of threats, including viruses, rootkits, worms and spyware
Optional cloud-powered scanning:
Whitelisting of safe files based on file reputation database in the cloud for better detection and faster scanning. Only information about executable and archive files is sent to the cloud – such data are not personally attributable.
Virtualization Support
ESET Shared Local Cache stores metadata about already scanned files within the virtual environment so identical files are not scanned again, resulting in boosted scan speed.
ESET module updates and virus signatures database are stored outside of the default location, so these don’t have to be downloaded every time a virtual machine is reverted to default snapshot.
Host-Based Intrusion Prevention System (HIPS)
Enables you to define rules for system registry, processes, applications and files. Provides anti-tamper protection and detects threats based on system behavior.
Exploit Blocker
Strengthens security of applications such as web browsers, PDF readers, email clients or MS office components, which are commonly exploited.
Monitors process behaviors and looks for suspicious activities typical of exploits.
Strengthens protection against targeted attacks and previously unknown exploits, i.e. zero-day attacks that could be used by crypto-ransomware to enter the targeted system.
Advanced Memory Scanner
Monitors the behavior of malicious processes and scans them once they decloak in the memory. This allows for effective infection prevention, even from heavily obfuscated malware,
often detecting crypto-ransomware prior to it encrypting valuable files.
Client Antispam
Effectively filters out spam and scans all incoming emails for malware. Native support for Microsoft Outlook (POP3, IMAP, MAPI).
Cross-Platform Protection
ESET security solutions for Windows are capable of detecting Mac OS threats and vice-versa, delivering better protection in multi-platform environments.
Web Control
Limits website access by category, e.g. gaming, social networking, shopping and others. Enables you to create rules for user groups to comply with your company policies.
Soft blocking – notifies the end user that the website is blocked giving him an option to access the website, with activity logged.
Anti-Phishing
Protects end users from attempts by fake websites to acquire sensitive information such as usernames, passwords or banking and credit card details.
Two-Way Firewall
Prevents unauthorized access to your company network. Provides anti-hacker protection and data exposure prevention. Lets you define trusted networks, making all other connections, such as to
public Wi-Fi, in ‘strict’ mode by default. Troubleshooting wizard guides you through a set of questions, identifying problematic rules, or allowing you to create new ones.
Vulnerability Shield
Improves detection of Common Vulnerabilities and Exposures (CVEs) on widely used protocols such as SMB, RPC and RDP.
Protects against vulnerabilities for which a patch has not yet been released or deployed.
Botnet Protection
Protects against infiltration by botnet malware – preventing spam and network attacks launched from the endpoint.
Device Control
Blocks unauthorized devices (CDs/DVDs and USBs) from your system. Enables you to create rules for
user groups to comply with your company policies. Soft blocking – notifies the end user that his device is blocked and gives him the option to access the device, with activity logged.
Idle-State Scanner
Aids system performance by performing a full scan proactively when the computer is not in use. Helps speed up subsequent scans by populating the local cache.
First Scan after Installation
Provides the option to automatically run low priority on-demand scan 20 minutes after installation, assuring protection from the outset.
Update Rollback
Lets you revert to a previous version of protection modules and virus signature database.
Allows you to freeze updates as desired - opt for temporary rollback or delay until manually changed.
Postponed Updates
Provides the option to download from three specialized update servers: pre-release (beta users), regular release (recommended for non-critical systems) and postponed release (recommended for company- critical systems – approximately 12 hours after regular release).
Local Update Server
Saves company bandwidth by downloading updates only once, to a local mirror server.
Mobile workforce updates directly from ESET Update Server when the local mirror is not available. Secured (HTTPS) communication channel is supported.
RIP & Replace
Other security software is detected and uninstalled during installation of ESET Endpoint solutions. Supports both 32 and 64-bit systems.
Customizable GUI Visibility
Visibility of Graphical User Interface (GUI) to end user can be set to: Full, Minimal, Manual or Silent. Presence of ESET solution can be made completely invisible to end user, including no tray icon or notification windows.
By hiding the GUI completely, the “egui.exe” process does not run at all, resulting in even lower system resource consumption by the ESET solution.
ESET License Administrator
Makes it possible to handle all licenses transparently, from one place via web browser. You can merge, delegate and manage all licenses centrally in real-time, even if you are not using ESET Remote Administrator.
Touchscreen Support
Supports touch screens and high-resolution displays.
More padding for and complete rearrangement of GUI elements. Basic frequently used actions accessible from tray menu.
Low System Demands
Delivers proven protection while leaving more system resources for programs that end users regularly run. Can be deployed on older machines without the need for an upgrade, thereby extending hardware lifetime. Conserves battery life for laptops that are away from the office, using battery mode.
Right-to-Left Language Support
Native right-to-left language support (e.g. for Arabic) for optimum usability.
Remote Management
ESET Endpoint solutions are fully manageable via ESET Remote Administrator.
Deploy, run tasks, set up policies, collect logs, and get notifications and an overall security overview of your network – all via a single web-based management console.
- 17% Off
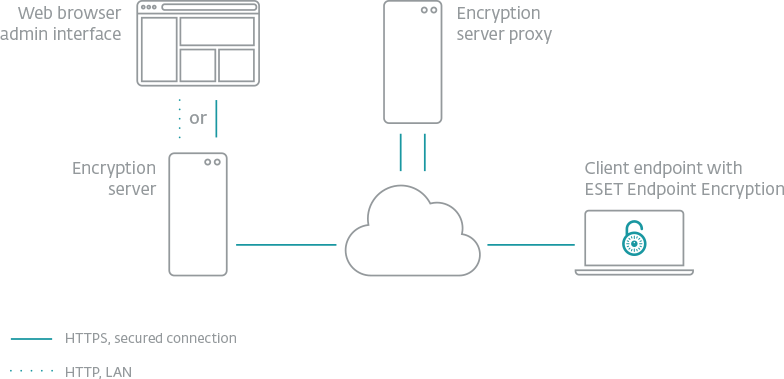
The ESET difference
No server required
ESET Endpoint Encryption requires no server for deployment and can seamlessly support remote users.
No special hardware required
TPM chips are optional but not required for using full disk encryption.
Fully validated
ESET Endpoint Encryption is FIPS 140-2 validated with 256 bit AES encryption.
Multi-platform
Encryption supported across Windows 10, 8, 8.1, 7, Vista, XP, and Server 2003 – Server 2016 and iOS.