- 47% Off
Cloud Email security powered by artificial intelligence Sophos Email is cloud email security simply delivered through Sophos Central’s easy-to-use single management console. Protecting your people from unwanted and malicious email threats today, and tomorrow, with the latest artificial intelligence.
Highlights
- Predictive email security able to block known and unknow threats
- Stop ransomware, spam, and phishing attacks
- Support for all major platforms
- Automatic Active Directory Synchronization
- Self-Service Portal with end-user and admin controls
Smarter Email Security
Today’s email threats move fast, and malicious files look more and more like benign files. Growing businesses need predictive email security - defeating today’s threats with an eye on tomorrow.
See the Future
Using the same technology as our award-winning Intercept X, the artificial intelligence built into Sophos Email’s Sandstorm sandboxing technology is a deep learning neural network, able to detect suspicious payloads containing threats, malware and unwanted applications, as well as high-level threats embedded in documents, including ransomware.
Sophos Sandstorm detonates these files in series of virtual machines, simulating a real end user environment where behavior can be monitored. Delivering safe documents – not just PDFs.
Block Stealth Attacks
Protecting employees from malicious website links, our advanced URL protection is out-smarting attackers who slip phishing URLs past traditional gateways - delaying the upload of malware to websites until after the email is delivered. Sophos Time-ofClick checks website reputation before delivery and at the time you click – blocking stealthy, delayed attacks.
Trust Your Inbox
Attackers relentlessly target organizations with spam, phishing, and advanced socially engineered attacks. Automate phishing imposter defense with Sophos Email authentication. Protecting your employees from phishing attacks using fraudulent email addresses that impersonate trusted contacts and domains, before they reach the inbox.
Using a combination of SPF, DKIM and DMARC authentication techniques and email header analysis, Sophos Email allows you to identify and allow legitimate emails from trusted partners, and block the imposter – allowing you to trust your inbox again.
Flexible Deployment
Sophos Email was born to be flexible. Creating unique security policies for individuals, groups or the whole domain can be done in minutes – saving you valuable time.
While seamless integration with Microsoft Office 365, Google G Suite, on-premises Exchange 2003+, and many more email providers, allows you to protect any email service where you control the domain and DNS records. Best of all - activation is completely in your control, with administrator controls and end-user self-service for common day-to-day tasks.
Secure Office 365
The answer for business-grade email. Email, Office, Collaboration – Microsoft Office 365 is a great tool for businesses to stay productive. But as customers move to O365, the security features often don’t live up to expectations. Great collaboration needs great security, and Sophos Email provides a simple solution:
- One Advanced license secures Office 365 from the latest spam, phishing and advanced threats
- Ensure compliance with a choice of location for email scanning and sandbox analysis
- Single easy-to-use management console
Getting Started is Easy
Deployment requires a simple MX record change to route email through Sophos Central, and you can simply bring in users and their mailboxes with our handy Azure and on premise Active Directory synchronization tools.
- 42% Off
Reduce your largest attack surface
Your end users are the most likely target for malware attacks. Keep your information safe with effective security awareness testing and training. Automate defense education for your users with routine campaigns, training, follow-up, and reporting.
Highlights
- Managed simulated phishing campaigns
- On-demand phishing assessments
- Personalized training for end users caught in a simulated attack
- Automated reporting on phishing and training results
Information security is only as secure as your weakest link Attackers relentlessly target end users with spear-phishing, spam, and sociallyengineered attacks. More than 90% of ransomware attacks are delivered via these types of email messages. Sophos Phish Threat emulates basic and advanced phishing attacks to help you identify areas of weakness in your organization’s security posture.
Easy campaign generation Simulate phishing, credential harvesting, or malware attacks in a few clicks. You’ll be up and running in minutes with constantly updated and socially relevant templates. Campaigns can be distributed broadly or targeted at specific roles in your organization like HR, Finance, and other departments.
Effective training modules Training modules are designed to educate about specific threats such as suspicious emails, credential harvesting, password strength, and regulatory compliance. Your end users will find them informative and engaging, while you’ll enjoy peace of mind when it comes to future real-world attacks.
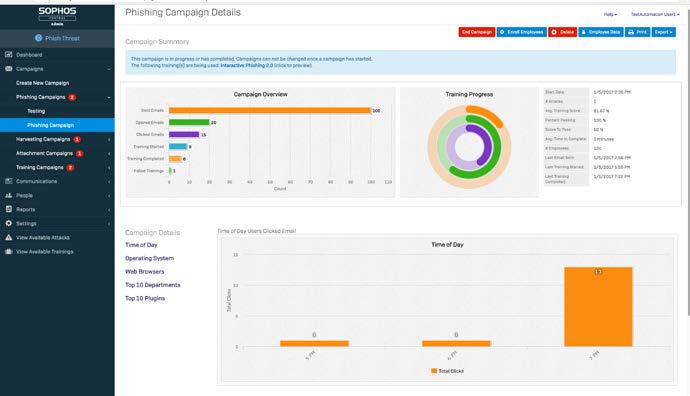
Comprehensive reporting The Phish Threat dashboard reports on results by company, department, and individual users, providing your entire IT organization with insight into individual performance and company-wide security posture alike.
- 47% Off
Reduce your largest attack surface
Your end users are the most likely target for malware attacks. Keep your information safe with effective security awareness testing and training. Automate defense education for your users with routine campaigns, training, follow-up, and reporting.
Highlights
- Managed simulated phishing campaigns
- On-demand phishing assessments
- Personalized training for end users caught in a simulated attack
- Automated reporting on phishing and training results
Information security is only as secure as your weakest link Attackers relentlessly target end users with spear-phishing, spam, and sociallyengineered attacks. More than 90% of ransomware attacks are delivered via these types of email messages. Sophos Phish Threat emulates basic and advanced phishing attacks to help you identify areas of weakness in your organization’s security posture.
Easy campaign generation Simulate phishing, credential harvesting, or malware attacks in a few clicks. You’ll be up and running in minutes with constantly updated and socially relevant templates. Campaigns can be distributed broadly or targeted at specific roles in your organization like HR, Finance, and other departments.
Effective training modules Training modules are designed to educate about specific threats such as suspicious emails, credential harvesting, password strength, and regulatory compliance. Your end users will find them informative and engaging, while you’ll enjoy peace of mind when it comes to future real-world attacks.
Comprehensive reporting The Phish Threat dashboard reports on results by company, department, and individual users, providing your entire IT organization with insight into individual performance and company-wide security posture alike.


- 57% Off
Securely connect anyone, anywhere, to any application. Sophos ZTNA transparently connects users to important business applications and data, providing enhanced segmentation, security, and visibility over traditional remote access VPN. It works as a standalone product and as a fully integrated Synchronized Security solution with Sophos Firewall and Intercept X.
Improve Your
Security Posture
ZTNA improves your security posture and reduces your attack surface in many ways: removing vulnerable and old VPN clients and infrastructure, eradicating implicit trust, incorporating device health into access policy, preventing lateral movement across the network, making your apps invisible to attackers, and providing much better insights into user and application activity.
Enable Remote
Workers
Remote access VPN has served us well, but it was never designed for this new world. ZTNA offers a much better alternative for remote access by providing better security and threat protection, an easier and more scalable management experience, and a more transparent and frictionless experience for end-users.
Micro-Segment Your Applications
With VPN, you’re providing network access. With Sophos ZTNA, you’re only providing access to specific applications. We micro-segment your applications, users, and devices, and with the integration of device health into access policies and continuous authentication verification, you get much better security. This eliminates all of the of implicit trust and the lateral movement that comes with VPN.
Stop Ransomware and Other Threats
Hackers are leveraging poorly secured remote systems and VPN vulnerabilities to get a foothold on networks to deploy ransomware. Sophos ZTNA helps reduce the surface area and risk of a ransomware attack by removing a new and growing vector. With ZTNA, remote systems are no longer connected “to the network” and only have specific application access.
Onboard New Apps and Users Quickly
Sophos ZTNA is much leaner, cleaner, and therefore easier to deploy and manage than traditional remote access VPN. It enables better security and more agility in quickly changing environments with users coming and going - making day-to-day administration a quick and painless task and not a full-time job.
Control Access to SaaS
Apps
As an alternative or supplement to SaaS application allowed IP ranges, you can utilize ZTNA and your Azure AD identity provider to control access to important SaaS applications – blocking denied devices and unauthorized users from accessing important cloud apps and data.
Highlights:
- Zero trust: trust nothing, verify everything
- Integrated with Sophos Intercept X
- Single agent, single console solution
- The ultimate remote-access VPN replacement
- Micro-segment and secure your network applications
- Works anywhere, on the network or off
- Cloud-managed, clouddelivered
- Transparent for end users
- Superior visibility and insights into your applications
- Integrates device health into access policies
- Simpler per-user annual subscription licensing with free gateways