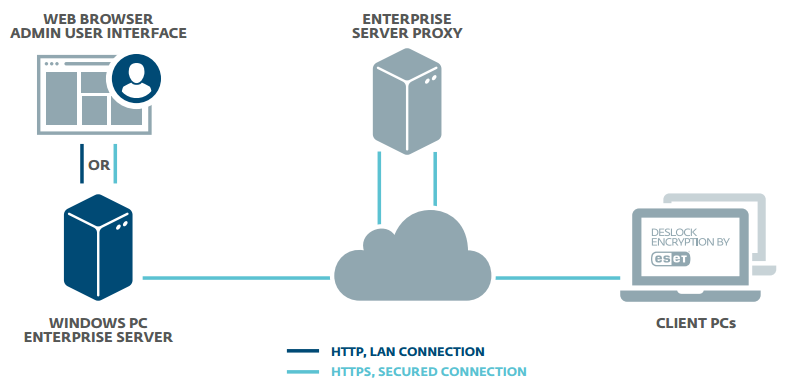
COMPLETE MAC SECURITY
Multi-layered and customizable security continuously keeps your Mac safe against worms, Trojans and other malicious programs without slowing it down.
Our Mac security software allows you to exclude files and folders from scanning and choose from comprehensive full-system or selective scan options. Allows you to quarantine suspected files and have a backup of files before repairing them.
PARENTAL CONTROL
This Mac antivirus software gives you the power to control, schedule and manage Internet access for your kids. You can block websites based on their categories (e.g. Adult, Gaming, Social Networking, Chat, Shopping, etc.). You can also block access to known websites by blacklisting their URL. The Parental Control tool lets you schedule a fixed timetable for your kids to access the Internet. All these facilities work together to keep your kids safe from several online threats.
WEB SECURITY
Cloud-based Internet security restricts fake and phishing websites from stealing your personal or financial information. Automatically blocks fake, compromised, infected and phishing websites. This way, your Mac stays safe even if you accidentally click on a malicious or potentially dangerous link.
SINGLE PRODUCT KEY
If you are using Parallels Desktop for Mac, then this feature will allow you to use your existing product key of Total Security for Mac to activate your copy of Quick Heal Total Security for Windows, installed in your system.
ANTISPAM AND EMAIL SECURITY
Antispam blocks unwanted emails from reaching your inbox. Real-time cloud-based email security blocks emails that might carry suspicious and potentially dangerous links or attachments.
SELF-PROTECTION
Prevents Quick Heal product files from getting altered or modified by viruses and malware or tampered by other applications.
TRACKMYLAPTOP
The best Mac antivirus software also comes with a laptop tracker facility called TrackMyLaptop - it helps track your lost or stolen laptop. The service is a social initiative that comes with every desktop product of Quick Heal at no extra cost.
Kindly note that, Quick Heal users have to register their Quick Heal Product License key at the TrackMyLaptop portal to avail this facility. Non-Quick Heal users have to register their Laptop's MAC ID. To know more, visit - http://trackmylaptop.net/
REMOTE DEVICE MANAGEMENT (RDM)
A free portal where you can add your Quick Heal enabled device, view its current status, and get notified of any critical situation such as notifications for updates, virus protection, etc. Click here to visit the portal.