Technical Specifications
Compare the range of functions of the different Server from Sophos to protect your infrastructure. Not sure which protection best suits your business? We can advise you free of charge and without any obligation.

Windows 11 Home is designed for the everyday user. If you're using your PC for personal tasks like web browsing, document creation, and entertainment, this version is ideal. It includes all the essential features, such as the new Start Menu, taskbar, and virtual desktops.
OEM license: Is a Windows license that only can be used with a new computer, this license is embedded on the first machine it was installed to. And this type of license is not transferable.
In essence, Windows 11 Home is designed for the everyday user who needs a reliable, user-friendly operating system for personal use. Windows 11 Pro, on the other hand, is tailored for professionals and businesses, offering advanced security, networking, and virtualization features.
With Sophos Central Intercept X for servers with XDR, you equip your servers with the maximum protection Sophos has to offer for servers. It includes all the functions of classic "Server Protection" with "Intercept X" for protection against ransomware and exploits, allowing you to protect your server environment against encryption Trojans. As the name of the product suggests, you also buy the "XDR" function.
XDR means "Extended Detection and Response" and is interesting for all those who want to get to the bottom of the cause of an attack in more detail, or in certain companies also have to. XDR is used, for example, when malware has been blocked or an exploit has been prevented. It could be that a thwarted attack is just a harbinger of a much larger attack. In our view, XDR can be seen as an extension of the "root cause analysis" already included in Intercept X, simply with many more options.
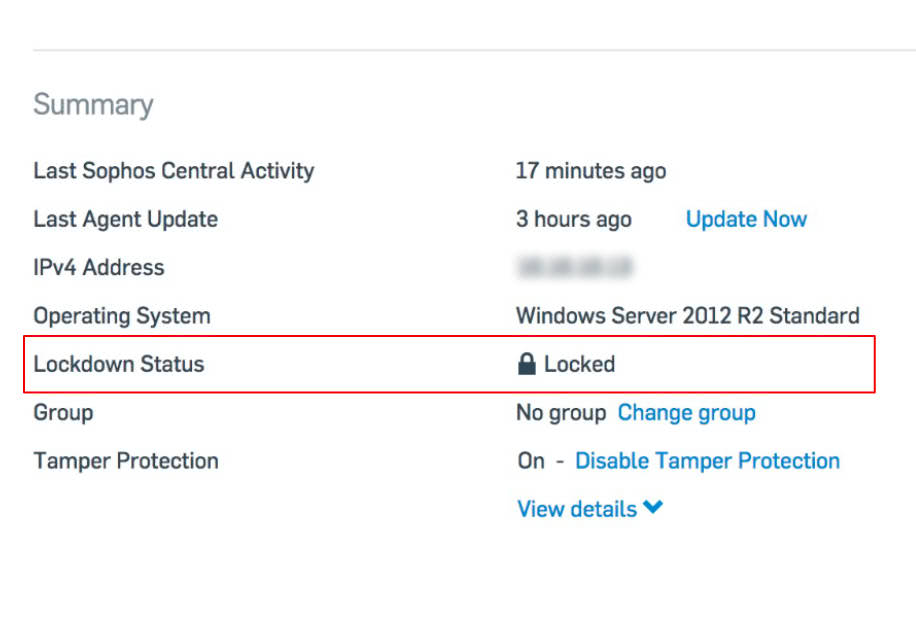
The Server lockdown gives you the benefit of one-click whitelisting. Once you activate the lockdown for your Server, it will first check if the system is threat-free. After that, it is necessary to record the current state of your server and create the whitelisting. All this happens in the background and does not affect the availability of your server. After one or two hours, indexing is usually complete and the system is in lockdown mode. From this point on, no software, including malware, can be installed on the system.
After lockdown, you can define so-called "update applications". For example, an update of an ERP can be such an update application. Windows updates are already whitelisted automatically and are allowed to update system components of Windows.
A classic antivirus doesn't stand a chance against encryption Trojans such as Petya, WannaCry or Locky. With CryptoGuard you get a technology on your Server that detects as soon as a ransomware tries to encrypt files on your Server and stops this process immediately. Already encrypted files are automatically restored afterwards, so that no data loss occurs.
CryptoGuard is the ideal complement to classic virus detection and is included as an additional layer of protection in Sophos intercept X for Server.
Find out the cause of the attack.
Imagine that, despite all the protective measures, malware has made it into your network. How could this happen? Thanks to the root cause analysis in Intercept X, this mystery can be uncovered with an impressive 360-degree analysis. The Root Cause Analysis Tool can tell you in great detail how the malware got into your network, which devices were infected and what steps you should take now.
With root cause analysis, you'll never be in the dark again if your network has been infected by an unknown malware.
Preventing the exploitation of security vulnerabilities.
Sophos Exploit Protection is a unique technology in Intercept X that prevents previously unknown or unpatched vulnerabilities in applications or operating system components from being exploited. With Intercept X, every application is monitored in the background and every action is checked to see if an exploit technique is being attempted.
If such a technique is detected, Exploit Prevention prevents a vulnerability from being exploited and restores the system to a secure state.
Compare the range of functions of the different Server from Sophos to protect your infrastructure. Not sure which protection best suits your business? We can advise you free of charge and without any obligation.
TallyPrime is a business software solution that is the latest version of Tally and replaces Tally ERP 9. Designed for businesses, TallyPrime provides users with the ability to gain insights from anywhere, anytime, and on any device. Its new features, including a powerful search bar called “Go-To” and multitasking capabilities, make it easier to manage invoicing, accounting, inventory, banking, tax, payroll, and more. TallyPrime offers a completely new look while maintaining its traditional values, making it a user-friendly option for businesses. Its secure data and in-depth business reports are some of the many features that make TallyPrime a useful tool for businesses.
Tally Prime is a comprehensive business management software that offers several features to support the daily operations of businesses.
Your growth Partner
To grow your business, and to make the right business decisions, you need the right insights . With features like “Go To” and “customisable reports” in the new TallyPrime, you can discover and look at reports, slicing and dicing them the way you want. To help you in your growth journey, Tally Prime enables you to manage multiple companies and incrementally add features such as multiple go-downs, multi-currency, order process, cost centres etc. This helps you get rid of complexities, and in turn, focus on business growth.
Quick and hassle-free bills receivables and payable management help you to get paid faster as well as managing payment timelines. Also, Tally facilitates easy and efficient stock movement, making it possible to optimize the cash flow. Besides, the insightful reports at blink of eye help you make confident decisions and plan the growth of your business better.
With the speed that Tally brings, you can get things done quickly and save precious time, helping you do more for less. With TallyPrime, you can print or view the reports being in the middle of voucher entry, you can load another company being in a report without abandoning the activity you were on it, get to know the irregularities or odd details from every reports that you view and much more. No more remembering short cut keys, you have the intuitive and consistent workflow that helps you do work faster.
Tally’s Prevention, Detection and Correction mechanism ensures that your books are always accurate, hence giving you the confidence that the returns you file are always correct!
McAfee Complete Data Protection—Advanced 1 McAfee Complete Data Protection—Advanced Comprehensive data protection anywhere, anytime Sensitive data is constantly at risk of loss, theft, and exposure. Many times, the data simply walks right out the front door on a laptop or USB device. Companies that suffer such a data loss risk serious consequences, including regulatory penalties, public disclosure, brand damage, customer distrust, and financial losses. The rapid proliferation of mobile devices with large storage capacities and often internet access is opening up even more channels for data loss or theft, so protecting sensitive, proprietary, and personally identifiable information must be a top priority. McAfee® Complete Data Protection—Advanced addresses all of these concerns and many more
Data Loss Prevention for Greater Control Preventing data loss at the endpoint begins with improving visibility and control over your data, even when it is disguised. McAfee Complete Data Protection— Advanced enables you to implement and enforce company-wide security policies that regulate and restrict how your employees use and transfer sensitive data via common channels, such as email, IM, printing, and USB drives. It does not matter if they are in the office, at home, or on the move—you stay in control.
Enterprise-Grade Drive Encryption Secure your confidential data with an enterprise-grade security solution that is FIPS 140-2 and Common Criteria EAL2+ certified and accelerated with the Intel Advanced Encryption Standard—New Instructions (Intel AES-NI) set. McAfee Complete Data Protection—Advanced uses drive encryption combined with strong access control via two-factor pre-boot authentication to prevent unauthorized access to confidential data on endpoints, including desktops, virtual desktop infrastructure (VDI) workstations, laptops, USB drives, CD/DVDs, and more.
Removable Media, File and Folder, and Cloud Storage Encryption Ensure that specific files and folders are always encrypted, regardless of where data is edited, copied, or saved. McAfee Complete Data Protection—Advanced features content encryption that automatically and transparently encrypts the files and folders you choose on the fly—before they move through your organization. You create and enforce central policies based on users and user groups for specific files and folders without user interaction.
Centralized Security Management and Advanced Reporting Use the centralized McAfee ePO software console to implement and enforce mandatory, company-wide security policies that control how data is encrypted, monitored, and protected from loss. Centrally define, deploy, manage, and update security policies that encrypt, filter, monitor, and block unauthorized access to sensitive data.
Key Advantages ■ Gain control over your data by monitoring and regulating how employees use and transfer data via common channels, such as email, IM, printing, and USB drives—both in and away from the office. ■ Stop data loss initiated by sophisticated malware that hijacks sensitive and personal information. ■ Secure data when it’s stored on desktops, laptops, tablets, and in the cloud. ■ Manage Apple FileVault and Microsoft BitLocker native encryption on endpoints directly from MVISION ePO or McAfee ePO software. ■ Communicate with and take control of your endpoints at the hardware level—whether they are powered off, disabled, or encrypted—to halt desk-side visits and endless help desk calls due to security incidents, outbreaks, or forgotten encryption passwords. ■ Prove compliance with advanced reporting and auditing capabilities. Monitor events and generate detailed reports that show auditors and other stakeholders your compliance with internal and regulatory privacy requirements
Sophos Central Intercept X Advanced is a combination of Sophos Central Endpoint Protection and Intercept X products.
With Sophos Central Intercept X Advanced, you get all the features of Sophos Central Endpoint Protection and Intercept X in one product.
On the one hand, you benefit from great functions such as "Peripheral Control" or "Malicious Traffic Detection", and at the same time you get a specialist on your computer with Intercept X, which uses a technology called "CryptoGuard" to detect as soon as malware tries to encrypt files on your computer and stops this process immediately. Files that have already been encrypted are then automatically restored, so there is no data loss.
Would you like to see the Sophos Central user interface live? Just go to central.sophos.com and use the demo account. Username: demo@sophos.com / Password: Demo@sophos.com
Preventing the exploitation of security vulnerabilities.
Sophos Exploit Protection is a unique technology in Intercept X that prevents previously unknown or unpatched vulnerabilities in applications or operating system components from being exploited. With Intercept X, every application is monitored in the background and every action is checked to see if an exploit technique is being attempted.
If such a technique is detected, Exploit Prevention prevents a vulnerability from being exploited and restores the system to a secure state.
Find out the cause of the attack.
Imagine that, despite all the protective measures, malware has made it into your network. How could this happen? Thanks to the root cause analysis in Intercept X, this mystery can be uncovered with an impressive 360-degree analysis. The Root Cause Analysis Tool can tell you in great detail how the malware got into your network, which devices were infected and what steps you should take now.
With root cause analysis, you'll never be in the dark again if your network has been infected by an unknown malware.
Restores the system to its original state after an attack.
With Intercept X, thanks to technologies like CryptoGuard, you are protected against signatureless malware, such as ransomware, but after an attempted attack, your system still needs to be cleaned of all remnants. Since there is no cleaning routine for unknown malware, the entire processes of the executed malware must be forensically examined. This task is performed by Sophos Clean.
Sophos Clean performs a complete cleaning of the system after an attack has been stopped. It not only removes the malware itself, but replaces infected Windows resources with more secure original versions and ultimately restores the system to its original state, as it was before the infection.
Compare the feature set of Sophos’s various endpoint products to protect your clients. Not sure which protection best suits your business? We advise you free of charge and completely without obligation.
Microsoft Surface Laptop 5
Get multitasking speed with 12th Gen Intel® Core™ processors built on
the Intel® Evo™ platform, long-lasting battery, and your choice of size and
colour in a sleek and beautiful touchscreen laptop design.
A sleek, beautiful,
timeless design
Between working from home and going out to auditions, Maya has a lot to
balance. But with Surface Laptop 5, she’s able to do it all in style.
Whether they’re working at the plant shop or creating sustainable
designs for friends, Luca and Reed need a laptop that can power their always-on
lifestyle.
Your business holds sensitive data that must be kept safe, which is why we do more than just protect every endpoint. Adaptive Security detects advanced threats, while server hardening enhances high-performance protection with additional application, web and device controls, to prevent the theft of corporate and financial information.
This tier includes all the functionality delivered by Kaspersky Endpoint Security for Business Select, plus additional advanced technologies that do even more to protect your business.
Identifies vulnerabilities and applies the latest patches to close attack entry-points, as well as letting you control which applications are allowed to run on your servers. Complemented by enterprise-grade web and device controls and a centralized security management console.
Endpoint detection and response capabilities that identify abnormal behavior, automatically detecting and remediating targeted ransomware and in particular fileless threats which try to mimic common behavior like PowerShell script execution.
Our Linux and Windows Server security has been developed specifically for application and terminal servers. Encryption functions – plus OS-embedded firewall and encryption management – guard corporate and customer information to help you achieve key compliance goals, including GDPR.
Automates software tasks including the creation, storage and cloning of system images – saving you time whenever you need to roll out new systems or update software on existing systems.
We’re pioneers in providing the highest levels of transparency and data sovereignty, as well as neutrality. We process core data in geopolitically neutral Switzerland, where our partners can review our source code.
Pinnacle Studio 26 (Standard) is one of the most popular video editing software. It is well accepted for video editing needs by both hobbyists as well as professional’s across the globe.
In terms of price, this software is much affordable than other video editing software’s, people who buy Pinnacle Studio 26 online can get more advantage because it has a more comprehensive interface and features that make it more impressive. Now, we can customize video creation with the help of dynamic video masking. It provides incredible effects, enhancements, and layering templates. Besides this, with Pinnacle Studio 26, we can do a lot of transformations. Even, we can also transform each section of the frame freely and independently. Furthermore, the latest update has significantly improved the masking tool. And, the Smart Edge tool has a lot of adjustment options that allow you to select and mask the object in any video clip with ease.
With the new title editor in Pinnacle Studio 26, the text graphic options have been greatly expanded. If you buy Pinnacle Studio 26 (Standard) online in India you can edit titles directly in the main video preview, which is a nice improvement over having to open a separate window previously. The degree of control over the titles is astounding. You can use keyframes to not only animate your names but also to add animation to particular words or letters within a title. You can animate graphics with your names, such as a lower thirds box to frame a caption, and you can apply and sync a light source with 3D title editing.
Moreover, you can upgrade your editing control over video clips, pictures, and backgrounds with the latest keyframing tools. Yet, this software provides you with in-depth keyframing controls. It is really helpful in creating stunning video creations or projects with precise sizes and positions.
If you choose to buy Pinnacle Studio 26 (Standard) online in India from technology surface, you will be able to avail a whole host of different benefits. The first benefit is the fact that our relationship with customers doesn’t just persist until the sale lasts. Instead, we at technology surface have dedicated customer support services that are always ready, willing, and able to help you with any concerns and questions you may have about your software.
Microsoft Surface Laptop 5
Get multitasking speed with 12th Gen Intel® Core™ processors built on
the Intel® Evo™ platform, long-lasting battery, and your choice of size and
colour in a sleek and beautiful touchscreen laptop design.
A sleek, beautiful,
timeless design
Between working from home and going out to auditions, Maya has a lot to
balance. But with Surface Laptop 5, she’s able to do it all in style.
Whether they’re working at the plant shop or creating sustainable
designs for friends, Luca and Reed need a laptop that can power their always-on
lifestyle.
Microsoft 365 Business Basic is perfect for the small or medium-sized business that needs advanced Office Applications, access for multiple people, business email, and shared file storage. This subscription does not include desktop Applications, so is best suited for a collaborative and mobile workforce with varying productivity, marketing, and organizational requirements.
Microsoft 365 Business Basic includes the fully installed advanced suite of Office Applications and 1TB of storage, with the following online and mobile only Applications:
Microsoft 365 Business Basic meets the needs of a multi-functional workforce that collaborates on files from the office, from home, and on the go.
Microsoft 365 Business Basic is an A-to-Z solution for remote teams that need to work together in real-time.
Microsoft 365 Business Basic makes it easy to secure and manage your sensitive business and or customer information.
Microsoft 365 Business Basic has a well-designed dashboard that business owners or IT managers can use to control all of the Microsoft Applications and services.
*Microsoft guarantees uptime (online availability) 99.9% of the time
Microsoft Surface Laptop 5
Get multitasking speed with 12th Gen Intel® Core™ processors built on
the Intel® Evo™ platform, long-lasting battery, and your choice of size and
colour in a sleek and beautiful touchscreen laptop design.
A sleek, beautiful,
timeless design
Between working from home and going out to auditions, Maya has a lot to
balance. But with Surface Laptop 5, she’s able to do it all in style.
Whether they’re working at the plant shop or creating sustainable
designs for friends, Luca and Reed need a laptop that can power their always-on
lifestyle.
With McAfee Complete Endpoint Protection — Business, you can spend more time on your business and less time worrying about security. This highly affordable, all-in-one solution provides top-rated endpoint security for all the devices in your enterprise: PCs, Macs, Linux systems, servers, virtual systems, smartphones, and tablets. Quickly and easily layer in protection against today’s most advanced threats, including encryption to protect your valuable data, behavioral zero-day intrusion prevention against attacks, hardware-enhanced protection against low-level, stealthy malware, and email, web, and mobile security to block phishing and multistage attacks. Easy installation and unified management reduce setup and maintenance. You can respond faster than ever.
Complete protection — Today, antivirus alone isn’t enough to defend against sophisticated, stealthy malware and attacks. The highest scoring vendor in an NSS Labs comparative test of current defenses against evasion attacks, McAfee finds, fixes, and freezes malware fast with multiple layers of protection. Hardware-enhanced system protection below the OS, available only from McAfee, targets stealthy attacks like rootkits that burrow deep into the kernel. And strong encryption secures your vital confidential data and prevents unauthorized access to PCs, Macs, laptops, and removable media — transparently and without slowing system performance. Behavior and reputation systems integrate with the cloud-based McAfee Global Threat Intelligence to protect against emerging cyberthreats across all vectors — file, web, message, and network.
Complete simplicity — With as few as four clicks and in as little as 20 minutes, you can be up and running. Web-based single console management with McAfee ePolicy Orchestrator software makes it easy to manage policies across all protections and systems and get instant visibility into security health across your entire infrastructure. With new real-time management, you can ask questions and fix vulnerabilities or correct problems faster than ever before.
Complete performance — Are you looking for security that supports business instead of slowing it down? Complete Endpoint Protection — Business minimizes security’s impact on users with fewer, smarter scans and advanced memory management. These technologies optimize CPU and memory usage to make strong security transparent to users across all platforms.
Defend all your endpoint devices, from traditional desktops and laptops to storage servers and mobile devices, with the industry’s highest scoring protection. McAfee® Complete Endpoint Protection—Business suite, an affordable, all-in-one solution, includes encryption to protect your valuable data, behavioral zero-day intrusion prevention for insidious exploits, hardware-enhanced protection against stealthy malware, as well as email, web, and mobile security to block phishing and multistage attacks. Single-console, web-based management eases the day-to-day burden on your IT staff and empowers them to act fast when threats strike.
Make endpoint security painless for your users and IT. McAfee Complete Endpoint Protection—Business helps growing organizations get security right, from turnkey installation to rapid response. With one unified solution, you cover all the devices in your enterprise—PCs, Macs, Linux systems, servers, smartphones, and tablets. Reduce complexity, cut costs, and protect against rootkits, mobile malware, targeted web and email attacks, and persistent threats. You get powerful, efficient protection and straightforward management that’s available only from McAfee, the market leader in endpoint security.
3-Year Subscription License. Includes all Product updates, Full version upgrades, Virus definition updates and technical support.
Symantec Endpoint Security Enterprise offers Industry-leading protection for all devices with cloud, on-premises, or hybrid management.
Symantec Endpoint Security Enterprise delivers the most complete, integrated endpoint security platform on the planet. As an on-premises, hybrid, or cloud-based solution, the single-agent Symantec platform protects all your traditional and mobile endpoint devices, and uses artificial intelligence (AI) to optimize security decisions. A unified cloud-based management system simplifies protecting, detecting and responding to all the advanced threats targeting your endpoints.
Click here to download a datasheet on Symantec Endpoint Security.
Liebert® GXT MT+ CX 16A is a true on-line UPS that delivers continuous, high-quality AC power to connected equipment with no interruption when transferring to battery. It provides protection from blackouts, Brownouts, sags, surges or noise interference. Liebert® GXT MT+ CX 16A is a full feature Transformer free UPS designed to o er compact, e icient and reliable solution to modern electronic gadgets. It features True Double Conversion On Line back up Power Solution for Small Data Centre, Data Networks, Voice Networks and Process automation equipment's. Liebert® GXT MT+ CX 16A provides customers with a reliable source of uninterruptible power even in harsh power environments, including very wide input voltage/frequency window, Better output voltage regulation, Frequency regulation, internal bypass, and input power factor correction and low THDi.
Liebert® GXT MT+ CX 16A UPS provides the capabilities often found only in larger systems. Get up to 3 kVA of capacity and battery backup. External battery cabinets may be added for extended run time. Liebert® GXT MT+ CX 16A UPS is a true on-line power source, which means power is always being conditioned and supplied to the connected device(s), whatever the quality of power coming in, a pure sine wave output results to ensure equipment is protected. Liebert GXT MT+ CX 16A UPS includes: • Front end IGBT based rectifier • Power factor correction • Frequency conversion • Eco mode • Inbuilt Over Voltage Cut-o Device (OVCD) • Internal automatic bypass to protect against adverse conditions • Support for up to 160 AH external battery cabinets